12 Data Loss Prevention Best Practices (+ Real Success Stories)
eSecurity Planet
APRIL 12, 2024
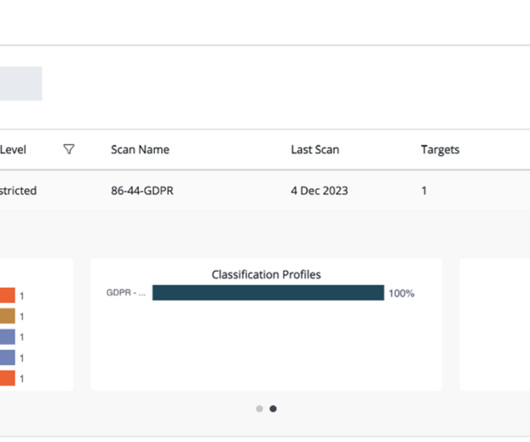
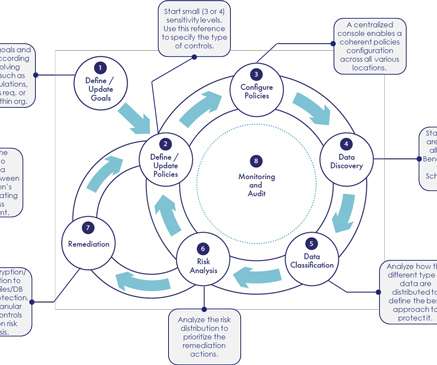
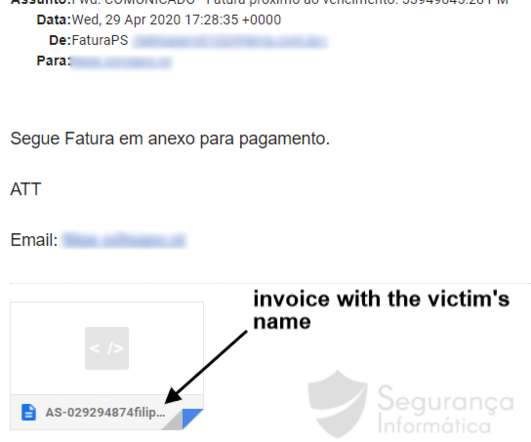
From tailoring your DLP policy to promoting a collaborative culture inside the organization, explore these established practices for a stronger data security approach. Tailor Your DLP Policy This approach begins with a thorough examination of the types of data that your business handles.















































Let's personalize your content