Moscow Military Hackers Used Microsoft Outlook Vulnerability
Data Breach Today
FEBRUARY 27, 2024
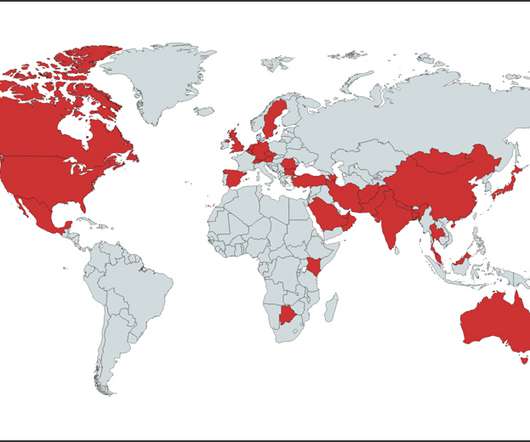
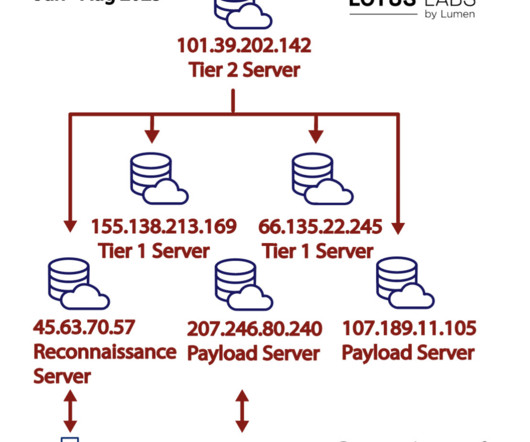
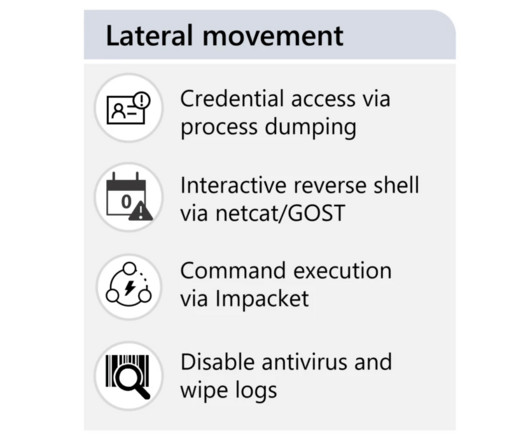
APT28 Used Hacked Ubiquiti Routers for Hashed Password Relay Attacks A campaign by Russian military intelligence to convert Ubiquiti routers into a platform for a global cyberespionage operation began as early as 2022, U.S. disrupted a botnet built by a hacking unit of Russian military's Main Intelligence Directorate.










































Let's personalize your content