Researchers Discover New Malware Aimed at Mining Sector
Data Breach Today
JULY 10, 2024
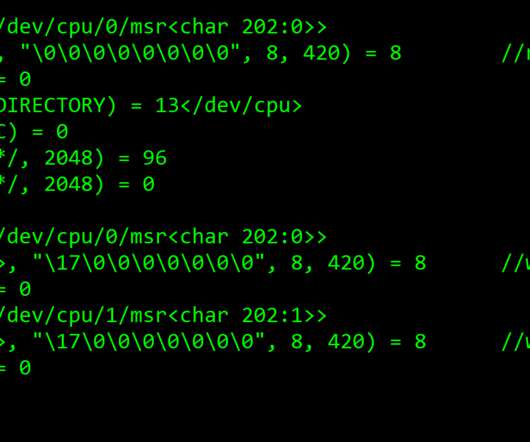
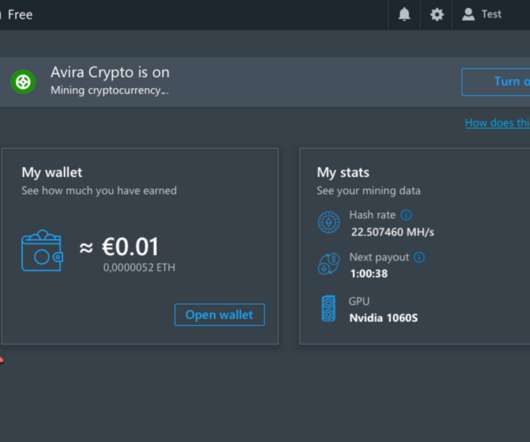
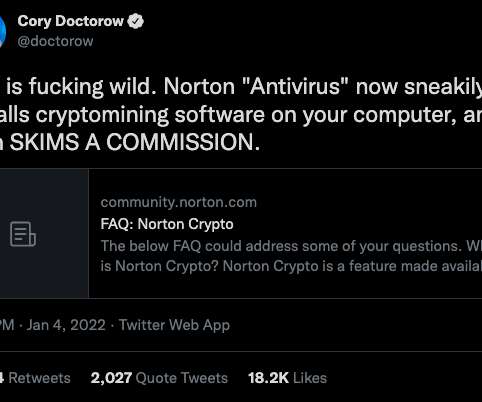
Remote Access Trojan 'Poco RAT' Targets Mining, Manufacturing Sectors, Says Report A new report published by Cofense Intelligence identifies a malware called "Poco RAT" that is actively targeting mining and manufacturing sectors across Latin America through a simple remote access Trojan that could be capable of delivering additional malware for ransomware (..)









































Let's personalize your content