Marriott Pays $52M to Settle US States Data Breach Litigation
Data Breach Today
OCTOBER 9, 2024
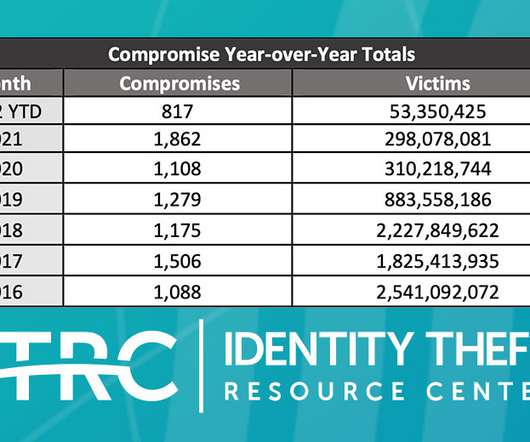
Hotel Chain Also Settles with Federal Trade Commission The world's largest hotel chain agreed Wednesday to pay $52 million and agree to two decades of third-party monitoring of its cybersecurity program to settle a rash of data breaches affecting millions of guests. The multi-million payout is part of a settlement reached with 50 U.S.


















































Let's personalize your content