NSA Offers Guidance on Adopting Encrypted DNS
Data Breach Today
JANUARY 15, 2021
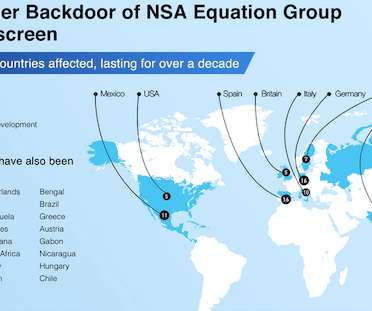
Agency Describes How DoH Can Help Prevent Eavesdropping The NSA has released guidance on how organizations can adopt encrypted domain name system protocols to prevent eavesdropping and manipulation of DNS traffic.


































Let's personalize your content