U.S. Treasury, Commerce Depts. Hacked Through SolarWinds Compromise
Krebs on Security
DECEMBER 14, 2020
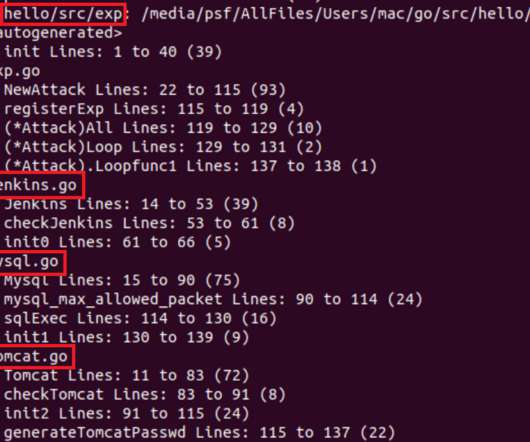
Communications at the U.S. Treasury and Commerce Departments were reportedly compromised by a supply chain attack on SolarWinds , a security vendor that helps the federal government and a range of Fortune 500 companies monitor the health of their IT networks. Given the breadth of the company’s customer base, experts say the incident may be just the first of many such disclosures.



































Let's personalize your content