What is Metadata and Why is it Important?
AIIM
MARCH 9, 2021
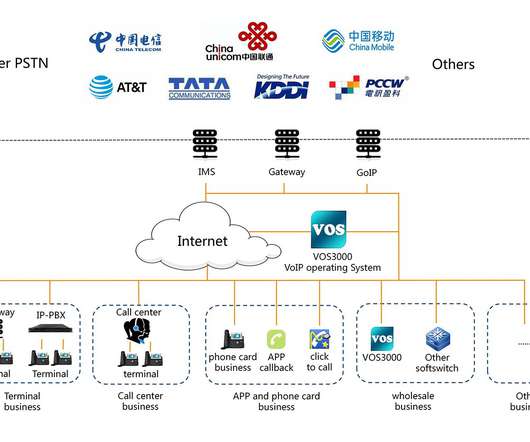
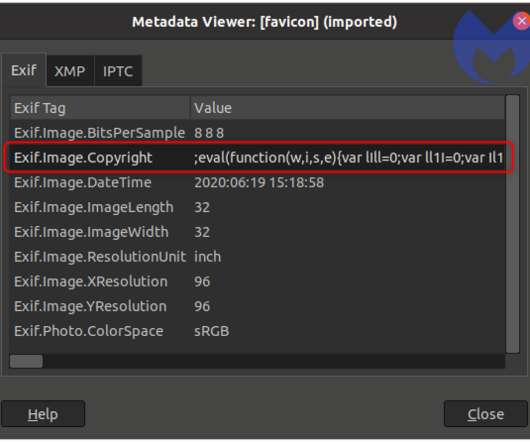
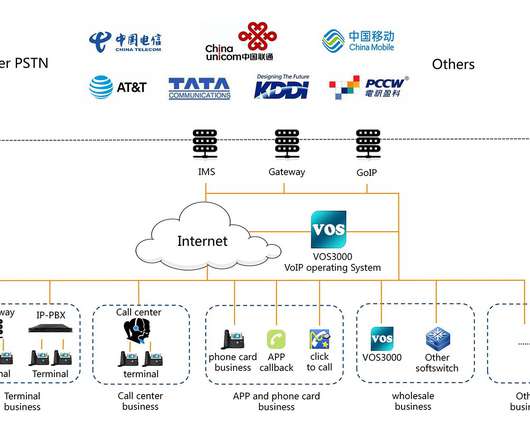
One such tool is Metadata. Metadata offers significant benefits in terms of understanding information in new ways and in being able to leverage that intelligence to drive innovation and the customer experience. What is Metadata? The US Department of Defense has a definition of metadata in its DoD 5015.2














































Let's personalize your content