FBI’s Vetted Info Sharing Network ‘InfraGard’ Hacked
Krebs on Security
DECEMBER 13, 2022
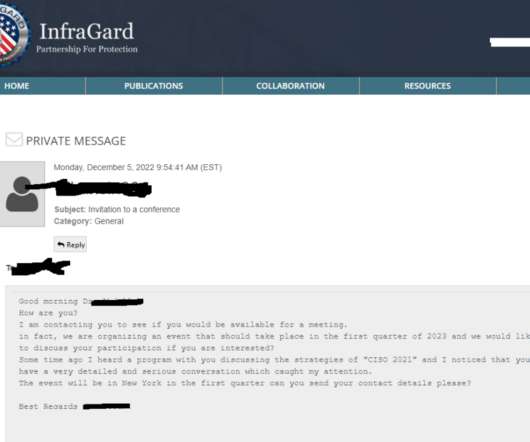
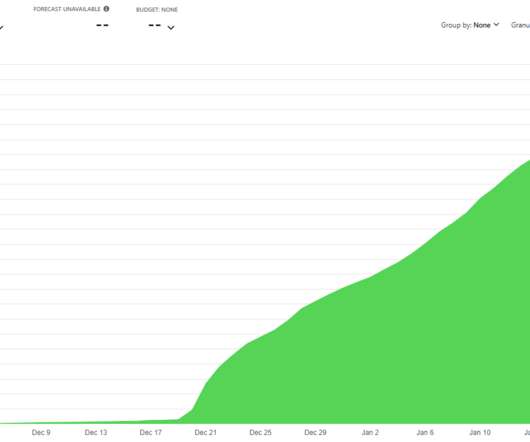
InfraGard , a program run by the U.S. Federal Bureau of Investigation (FBI) to build cyber and physical threat information sharing partnerships with the private sector, this week saw its database of contact information on more than 80,000 members go up for sale on an English-language cybercrime forum. Meanwhile, the hackers responsible are communicating directly with members through the InfraGard portal online — using a new account under the assumed identity of a financial industry CEO tha






































Let's personalize your content