Target Sues Insurer Over 2013 Data Breach Costs
Data Breach Today
NOVEMBER 21, 2019
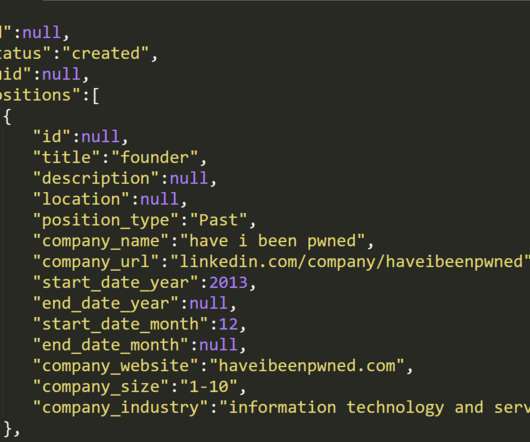
Lawsuit Claims Insurer Owes Retailer for Coverage of Card Replacement Costs Target has filed a lawsuit against its long-time insurer, ACE American Insurance Co., in an attempt to recoup money it spent to replace payment cards as part of settlements over the retailer's massive 2013 data breach. Find out how much money the company is seeking.




































Let's personalize your content