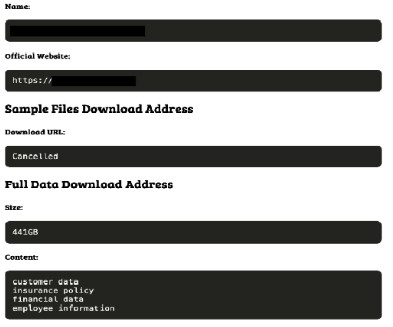
Australian Insurer Medibank Says Incident Was Ransomware
Data Breach Today
OCTOBER 17, 2022
Apparent Spate of Australian Data Breaches Continues Australian health insurer Medibank told investors it stopped a probable ransomware attack before the attack could steal data or maliciously encrypt its systems.











































Let's personalize your content