Cactus RANSOMWARE gang hit the Swedish retail and grocery provider Coop
Security Affairs
JANUARY 1, 2024
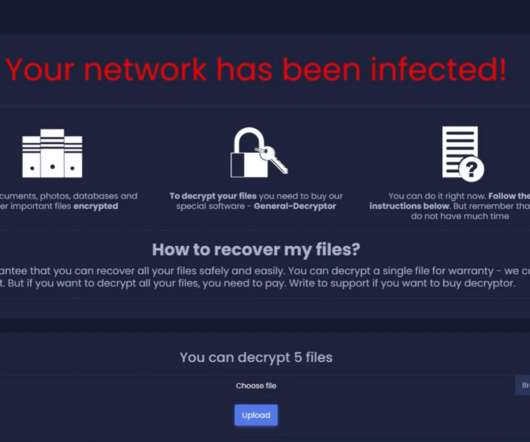
The Cactus ransomware group claims to have hacked Coop, one of the largest retail and grocery providers in Sweden. Coop is one of the largest retail and grocery providers in Sweden, with approximately 800 stores across the country. The stores are co-owned by 3.5 million members in 29 consumer associations.











































Let's personalize your content