Enterprise-managed IAM: An SRE team case study
IBM Big Data Hub
OCTOBER 24, 2023
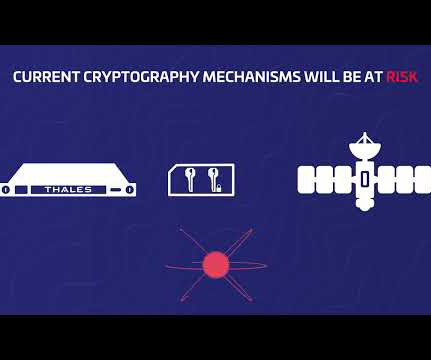
Enterprise-managed identity and access management (IAM) enables cloud administrators to centrally configure access and security settings for the entire organization. Case study A large banking client has a centralized site reliability engineering (SRE) team that manages operations for all resources in the organization.

















































Let's personalize your content