RSAC Fireside Chat: Reinforcing ‘Identity and Access Management’ to expose ‘shadow access’
The Last Watchdog
MAY 31, 2023
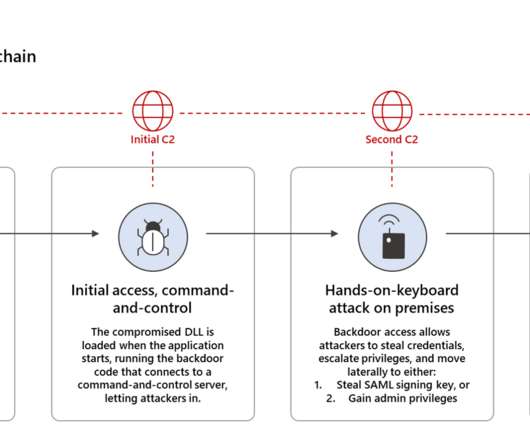
The world of Identity and Access Management ( IAM ) is rapidly evolving. Related: Stopping IAM threats IAM began 25 years ago as a method to systematically grant human users access to company IT assets. Today, a “user” most often is a snippet of code seeking access at the cloud edge.

















































Let's personalize your content