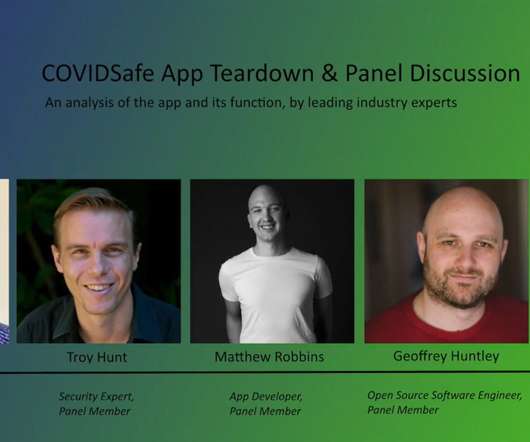
COVIDSafe App Teardown & Panel Discussion
Troy Hunt
APRIL 30, 2020
I've written a bunch about COVID-19 contact tracing apps recently as they relate to security and privacy, albeit in the form of long tweets. None of us have any commercial interests in this (we all went through a disclosure process in the video), it's just pure independent, fact-based discussion.













































Let's personalize your content