Why Your VPN May Not Be As Secure As It Claims
Krebs on Security
MAY 6, 2024
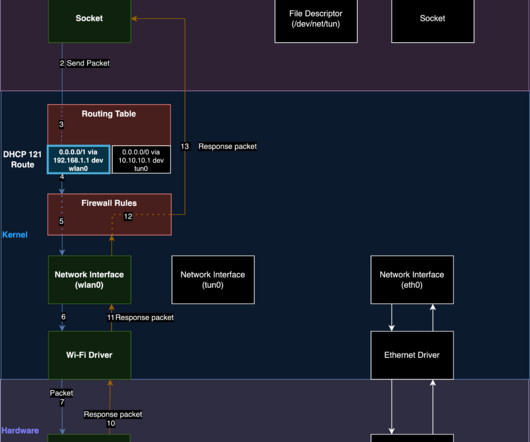
Virtual private networking (VPN) companies market their services as a way to prevent anyone from snooping on your Internet usage. But new research suggests this is a dangerous assumption when connecting to a VPN via an untrusted network, because attackers on the same network could force a target’s traffic off of the protection provided by their VPN without triggering any alerts to the user.






































Let's personalize your content