FBI Warns of AI-Assisted Phishing Campaigns
KnowBe4
MAY 15, 2024
The US Federal Bureau of Investigation’s (FBI’s) San Francisco division warns that threat actors are increasingly using AI tools to improve their social engineering attacks.

KnowBe4
MAY 15, 2024
The US Federal Bureau of Investigation’s (FBI’s) San Francisco division warns that threat actors are increasingly using AI tools to improve their social engineering attacks.

Data Breach Today
MAY 15, 2024
What It Means, Who Is Affected by It and How to Overcome It Imposter syndrome is a psychological phenomenon in which individuals doubt their accomplishments and have an internalized fear of being exposed as a fraud. Employees can overcome these fears by finding mentors, documenting achievements and engaging in continuous learning.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 16, 2024
Meeting the demands of the modern-day SMB is one of the challenges facing many business leaders and IT operators today. Traditional, office-based infrastructure was fine up until the point where greater capacity was needed than those servers could deliver, vendor support became an issue, or the needs of a hybrid workforce weren’t being met. Related: SMB brand spoofing In the highly competitive SMB space, maintaining and investing in a robust and efficient IT infrastructure can be one of the ways
Krebs on Security
MAY 14, 2024
Microsoft today released updates to fix more than 60 security holes in Windows computers and supported software, including two “zero-day” vulnerabilities in Windows that are already being exploited in active attacks. There are also important security patches available for macOS and Adobe users, and for the Chrome Web browser, which just patched its own zero-day flaw.

Advertisement
With its unparalleled flexibility, rapid development and cost-saving capabilities, open source is proving time and again that it’s the leader in data management. But as the growth in open source adoption increases, so does the complexity of your data infrastructure. In this Analyst Brief developed with IDC, discover how and why the best solution to this complexity is a managed service, including: Streamlined compliance with some of the most complex regulatory guidelines Simplified operations, li
Security Affairs
MAY 17, 2024
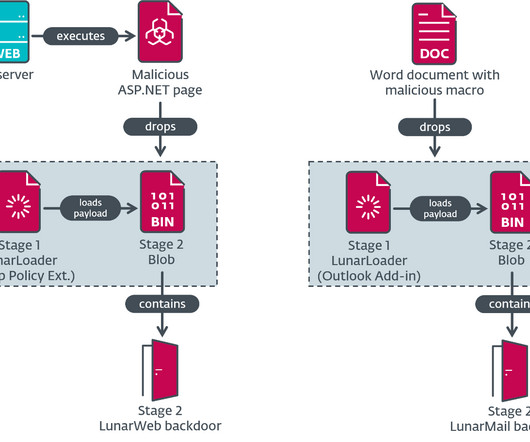
Russia-linked Turla APT allegedly used two new backdoors, named Lunar malware and LunarMail, to target European government agencies. ESET researchers discovered two previously unknown backdoors named LunarWeb and LunarMail that were exploited to breach European ministry of foreign affairs. The two backdoors are designed to carry out a long-term compromise in the target network, data exfiltration, and maintaining control over compromised systems.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

The Last Watchdog
MAY 16, 2024
Hardware-based cybersecurity solutions are needed to help defend company networks in a tumultuous operating environment. Related: World’s largest bank hit by ransomware attack While software solutions dominated RSA Conference 2024 and are essential for multi-layered defense of an expanding network attack surface, hardware security solutions can serve as a last line of defense against unauthorized access to sensitive data and tampering with systems.

WIRED Threat Level
MAY 13, 2024
Amid a rising tide of adversary drones and missile attacks, laser weapons are finally poised to enter the battlefield.

Security Affairs
MAY 13, 2024
Apple rolled out urgent security updates to address code execution vulnerabilities in iPhones, iPads, and macOS. Apple released urgent security updates to address multiple vulnerabilities in iPhones, iPads, macOS. The company also warns of a vulnerability patched in March that the company believes may have been exploited as a zero-day. The issue impacts older iPhone devices, it is tracked as CVE-2024-23296 and is a memory corruption flaw in the RTKit.
Data Breach Today
MAY 15, 2024
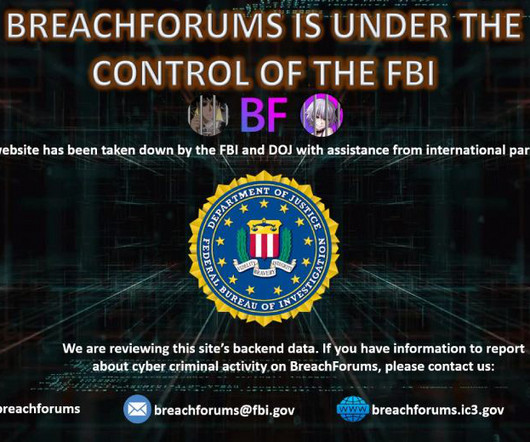
Website of BreachForums Administrator 'Baphomet' Also Appears to Be Down An international law enforcement operation shut down BreachForums, a criminal forum where hackers posted and sold the contents of hacked databases. The website of the criminal forum in its clear and dark web domains displays a seizure notice stating that it is "under the control of the FBI.

Advertisement
The complexity of financial data, the need for real-time insight, and the demand for user-friendly visualizations can seem daunting when it comes to analytics - but there is an easier way. With Logi Symphony, we aim to turn these challenges into opportunities. Our platform empowers you to seamlessly integrate advanced data analytics, generative AI, data visualization, and pixel-perfect reporting into your applications, transforming raw data into actionable insights.
The Last Watchdog
MAY 13, 2024
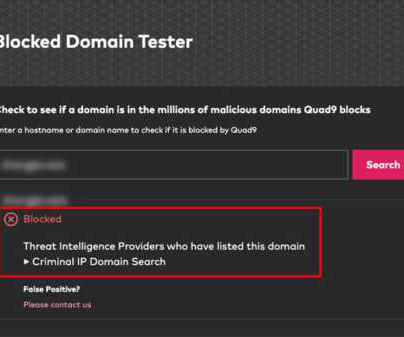
Torrance, Calif., May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users. Criminal IP underwent rigorous data evaluation to integrate with Quad9’s threat-blocking service, demonstrating high data uniqueness and accuracy.

KnowBe4
MAY 14, 2024
Trend analysis of ransomware attacks in the first quarter of this year reveals a continual increase in the number of "unknown" initial attack vectors, and I think I might understand why.

Security Affairs
MAY 14, 2024
Google released emergency security updates to address an actively exploited Chrome zero-day vulnerability. Google has released emergency security updates to address a high-severity zero-day vulnerability vulnerability, tracked as CVE-2024-4761, in the Chrome browser. The vulnerability is an out-of-bounds write issue that resides in the V8 JavaScript engine of the Google web browser.

Data Breach Today
MAY 16, 2024
Law Enforcment Arrests an Arizona Woman and a Ukrainian National U.S. law enforcement swept up two people and possibly hundreds of laptops used in scams by North Korean IT workers to obtain remote employment, including as contractors for an unnamed U.S. cybersecurity company. Prosecutors say one scam run by an Arizona woman netted Pyongyang at least $6.8 million.

Advertisement
Adding high-quality entity resolution capabilities to enterprise applications, services, data fabrics or data pipelines can be daunting and expensive. Organizations often invest millions of dollars and years of effort to achieve subpar results. This guide will walk you through the requirements and challenges of implementing entity resolution. By the end, you'll understand what to look for, the most common mistakes and pitfalls to avoid, and your options.

The Last Watchdog
MAY 13, 2024
London, United Kingdom, May 13, 2024, CyberNewsWire — Logicalis, the global technology service provider delivering next-generation digital managed services, has today announced the launch of Intelligent Security, a blueprint approach to its global security portfolio designed to deliver proactive advanced security for customers worldwide. Intelligent Security has been designed by Logicalis’ worldwide team of security specialists to give customers the most comprehensive observability a

WIRED Threat Level
MAY 13, 2024
NYC mayor Eric Adams wants to test Evolv’s gun-detection tech in subway stations—despite the company saying it’s not designed for that environment. Emails obtained by WIRED show how the company still found an in.

Security Affairs
MAY 16, 2024
The Spanish bank Santander disclosed a data breach at a third-party provider that impacted customers in Chile, Spain, and Uruguay. The Spanish financial institution Santander revealed a data breach involving a third-party provider that affected customers in Chile, Spain, and Uruguay. The bank recently became aware of unauthorized access to one of its databases hosted by a third-party provider.

Data Breach Today
MAY 16, 2024
Also: Turla Targets European Missions and Google Patches Chrome Zero-Days This week, hackers used a Linus backdoor and a Microsoft client management tool; Santander Bank, the Helsinki Education Division, an Australian energy provider and auction house Christie's were breached; hackers targeted European missions in the Middle East; and Google patched a zero-day flaw.

Speaker: Maher Hanafi, VP of Engineering at Betterworks & Tony Karrer, CTO at Aggregage
Executive leaders and board members are pushing their teams to adopt Generative AI to gain a competitive edge, save money, and otherwise take advantage of the promise of this new era of artificial intelligence. There's no question that it is challenging to figure out where to focus and how to advance when it’s a new field that is evolving everyday. 💡 This new webinar featuring Maher Hanafi, VP of Engineering at Betterworks, will explore a practical framework to transform Generative AI pr

Schneier on Security
MAY 14, 2024
Google has patched another Chrome zero-day: On Thursday, Google said an anonymous source notified it of the vulnerability. The vulnerability carries a severity rating of 8.8 out of 10. In response, Google said, it would be releasing versions 124.0.6367.201/.202 for macOS and Windows and 124.0.6367.201 for Linux in subsequent days. “Google is aware that an exploit for CVE-2024-4671 exists in the wild,” the company said.

KnowBe4
MAY 17, 2024
Regardless of whether your environment is on-premises, in the cloud or hybrid, new data makes it clear that users are the top cybersecurity concern, and we cover what you can do about it.

Security Affairs
MAY 12, 2024
Black Basta ransomware affiliates have breached over 500 organizations between April 2022 and May 2024, FBI and CISA reported. The FBI, CISA, HHS, and MS-ISAC have issued a joint Cybersecurity Advisory (CSA) regarding the Black Basta ransomware activity as part of the StopRansomware initiative. Black Basta has targeted at least 12 critical infrastructure sectors, including Healthcare and Public Health.

Data Breach Today
MAY 14, 2024
UK GCHQ Director Calls Chinese Hacking a 'Top Priority' Chinese-backed espionage and cyber disruption pose a major threat to global critical infrastructure as Beijing races for global edge, British and U.S. cyber officials warned Tuesday. Responding to the scale and complexity of Chinese hacking is a top British priority.

Advertisement
It’s no surprise that Apache Cassandra has emerged as a popular choice for organizations of all sizes seeking a powerful solution to manage their data at a scale—but with great power comes great responsibility. Due to the inherent complexity of distributed databases, this white paper will uncover the 10 rules you’ll want to know when managing Apache Cassandra.

WIRED Threat Level
MAY 13, 2024
Tuesday’s verdict in the trial of Alexey Pertsev, a creator of crypto-privacy service Tornado Cash, is the first in a string of cases that could make it much harder to skirt financial surveillance.

KnowBe4
MAY 16, 2024
A scam operation called “Estate” has attempted to trick nearly a hundred thousand people into handing over multi-factor authentication codes over the past year, according to Zack Whittaker at TechCrunch.
Security Affairs
MAY 13, 2024
A group of hackers that defines itself as “first-class Russian hackers” claims the defacement of hundreds of local and regional British newspaper websites. A group claiming to be “first-class Russian hackers” defaced numerous local and regional British newspaper websites owned by Newsquest Media Group. The group defaced the home pages of the targeted websites and posted the message “PERVOKLASSNIY RUSSIAN HACKERS ATTACK.” The following image shows an archived version of t

Data Breach Today
MAY 17, 2024
Covered Financial Institutions Have 30 Days to Notify Customers of Data Breaches The Securities and Exchange Commission unanimously approved updated regulations for covered financial institutions requiring entities such as fund companies and investment advisers to notify customers within 30 days of a cyber incident that compromised their data.

Advertisement
In the fast-moving manufacturing sector, delivering mission-critical data insights to empower your end users or customers can be a challenge. Traditional BI tools can be cumbersome and difficult to integrate - but it doesn't have to be this way. Logi Symphony offers a powerful and user-friendly solution, allowing you to seamlessly embed self-service analytics, generative AI, data visualization, and pixel-perfect reporting directly into your applications.

Schneier on Security
MAY 16, 2024
Microsoft is working on a promising-looking protocol to lock down DNS. ZTDNS aims to solve this decades-old problem by integrating the Windows DNS engine with the Windows Filtering Platform—the core component of the Windows Firewall—directly into client devices. Jake Williams, VP of research and development at consultancy Hunter Strategy, said the union of these previously disparate engines would allow updates to be made to the Windows firewall on a per-domain name basis.

KnowBe4
MAY 15, 2024
New data shows that despite the massive evolution of the cybercrime economy, threat actors are sticking with the basics in social engineering attacks, with a goal at stealing data.

Security Affairs
MAY 13, 2024
Experts reported that since April, the Phorpiex botnet sent millions of phishing emails to spread LockBit Black ransomware. New Jersey’s Cybersecurity and Communications Integration Cell (NJCCIC) reported that since April, threat actors used the the Phorpiex botnet to send millions of phishing emails as part of a LockBit Black ransomware campaign.
Let's personalize your content