Kalay cloud platform flaw exposes millions of IoT devices to hack
Security Affairs
AUGUST 17, 2021
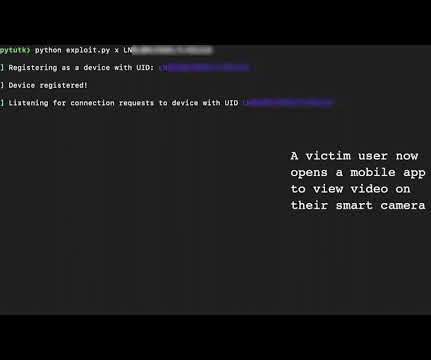
FireEye Mandiant researchers have discovered a critical vulnerability in the Kalay cloud platform that exposes millions of IoT devices to attacks. ” ThroughTek, the company that developed the cloud IoT platform, has released SDK updates to address the flaw. The company recommends its customers to enable AuthKey and DTLS.
















































Let's personalize your content