Law Enforcement's Cybercrime Honeypot Maneuvers Paying Off
Data Breach Today
JUNE 18, 2021
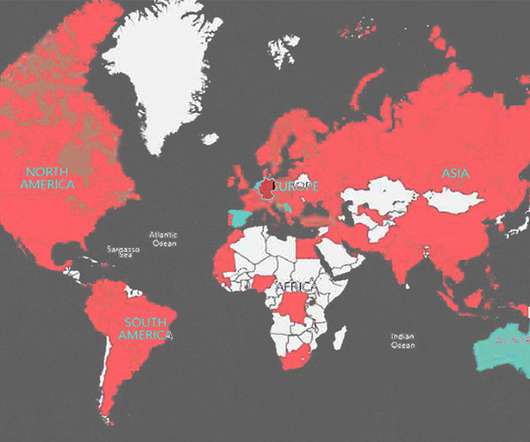
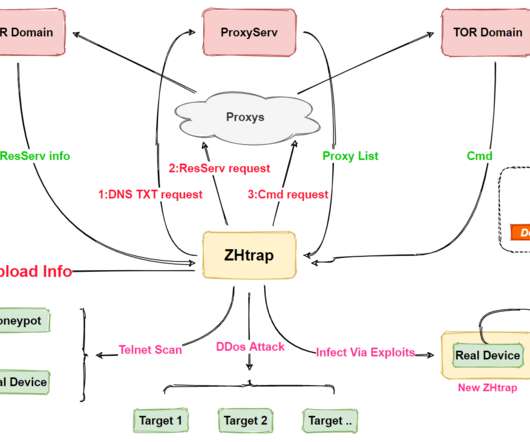
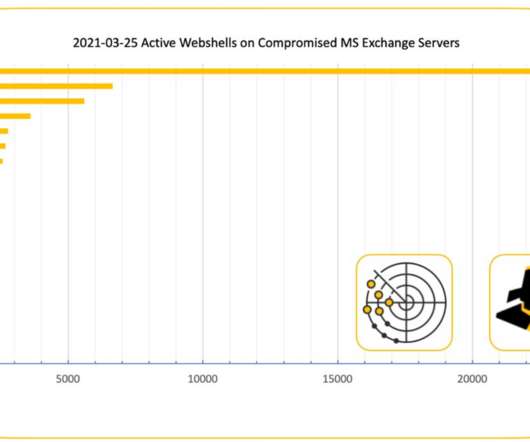
Closing EncroChat and Sky, Plus Careful Word-of-Mouth Management, Drove Anom Uptake The global law enforcement "Anom" honeypot operation racked up impressive statistics for the number of criminals tricked into using the encrypted communications service.


































Let's personalize your content