What Is Cloud Security Management? Types & Strategies
eSecurity Planet
MAY 30, 2024
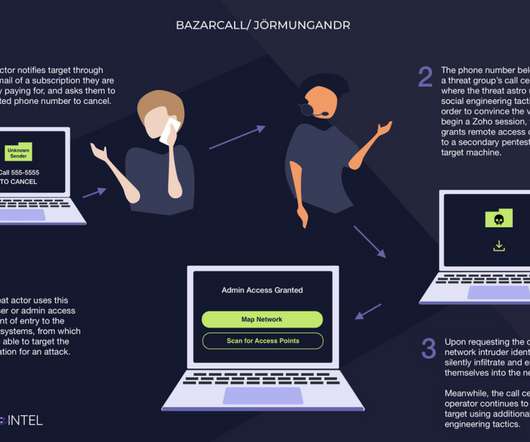
Cloud security management is the process of safeguarding cloud data and operations from attacks and vulnerabilities through a set of cloud strategies, tools, and practices. To maximize the benefits of cloud security management and counteract its challenges, apply effective strategies and tailored cloud security tools.


















































Let's personalize your content