What Is a Circuit-Level Gateway? Definitive Guide
eSecurity Planet
FEBRUARY 21, 2024
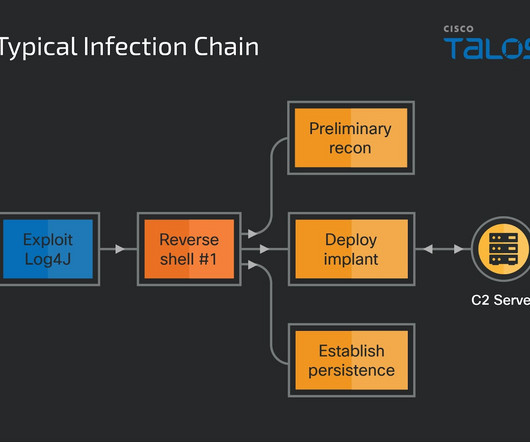
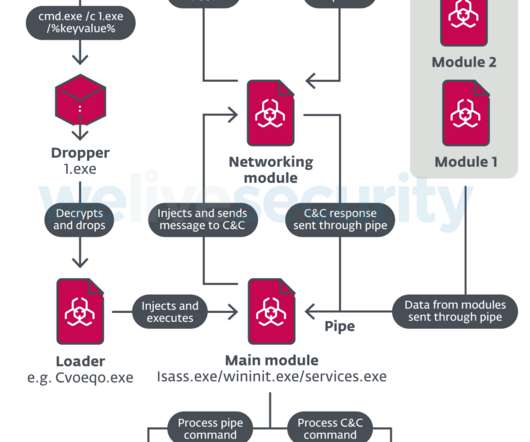
CLGs depend on two key features, proxy capability and stateful packet inspection, to block unsolicited communication. Successful implementation of a circuit-level gateway defends against unrestricted communication, which can enable network probing, malware delivery, and other attacks.















































Let's personalize your content