What Is Data Literacy?
erwin
AUGUST 6, 2020
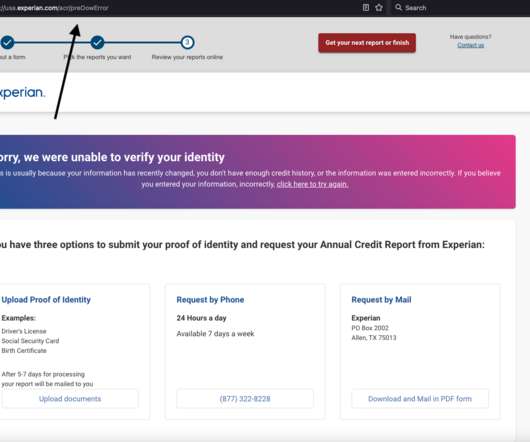
Data Literacy Definition. Gartner defines data literacy as the ability to read, write and communicate data in context, including an understanding of data sources and constructs, analytical methods and techniques applied — and the ability to describe the use case, application and resulting value. So, what is data literacy?


































Let's personalize your content