What is Vishing? Definition, Examples and Prevention
IT Governance
AUGUST 3, 2023
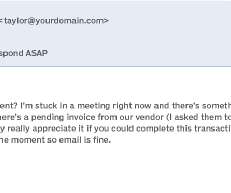
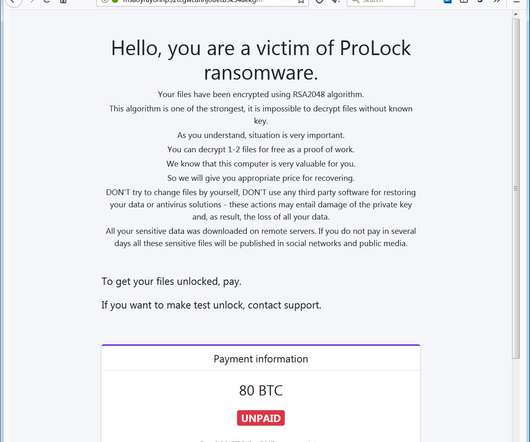
Posing as someone from a trusted organisation, such as a bank, they will create a sense of urgency, pressuring the recipient into giving up their details before they have a chance to think about what they are doing. They will request remote access to the device to perform a fake vulnerability scan to detect the “virus”.



















































Let's personalize your content