What is Smishing? Definition, Examples and Prevention
IT Governance
JULY 19, 2023
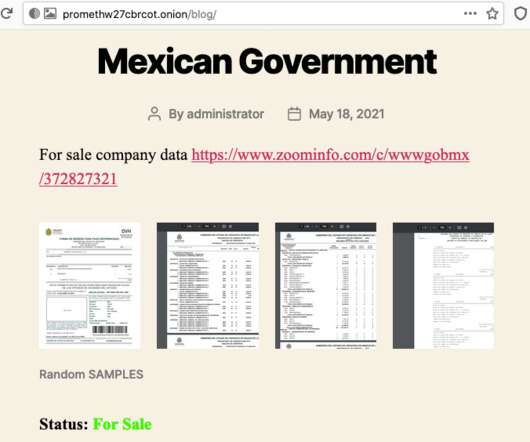
The scammer will try to gain your trust by claiming to be a figure of authority, such as the government or a well-known organisation. This can give them access to your sensitive information, and it’s why you should install malware protection. Definition, Examples and Prevention appeared first on IT Governance UK Blog.
















































Let's personalize your content