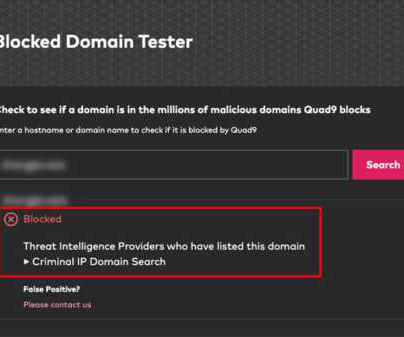
News alert: Criminal IP and Quad9 collaborate to exchange domain and IP threat intelligence
The Last Watchdog
MAY 13, 2024
of malicious domains identified by Criminal IP’s threat intelligence were found to be non-duplicative with other TI data. Enhanced threat blocking Quad9 is a free anycast DNS platform delivering robust security protections and privacy guarantees that comply with rigorous Swiss Data Protection and GDPR rules.































Let's personalize your content