ShrinkLocker Ransomware Exploits Microsoft's BitLocker
Data Breach Today
MAY 24, 2024
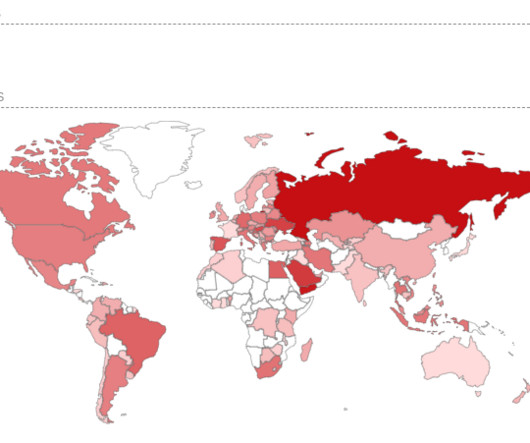
Malicious Script Targets Users in Mexico, Indonesia, Jordan Why bother building a crypto-locker when Microsoft has perfectly acceptable encryption software preloaded on desktops? Many ransomware hackers agree with that statement - and they're learning to make such attacks even harder to recover from.




































Let's personalize your content