Breach Roundup: Fluent Bit Flaw Is Risky for Cloud Providers
Data Breach Today
MAY 23, 2024
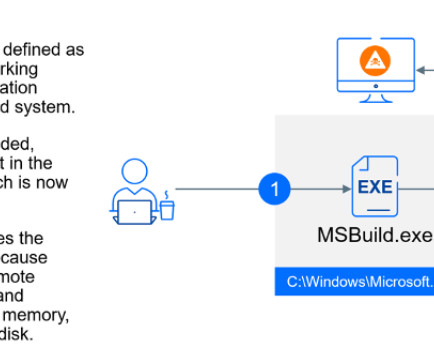
Also: Spanish Hacker Alcasec Arrested Again This week, Fluent Bit contains a flaw, Microsoft is nuking VBScript, Irish police and the SEC face fines, a man was sentenced for BEC, a flaw was found in Netflix's Genie, an Australia university said it was breached and Black Basta claimed an attack, and hacker Alcasec was arrested again.






































Let's personalize your content