GDPR and The Data Governance Imperative
AIIM
SEPTEMBER 12, 2018
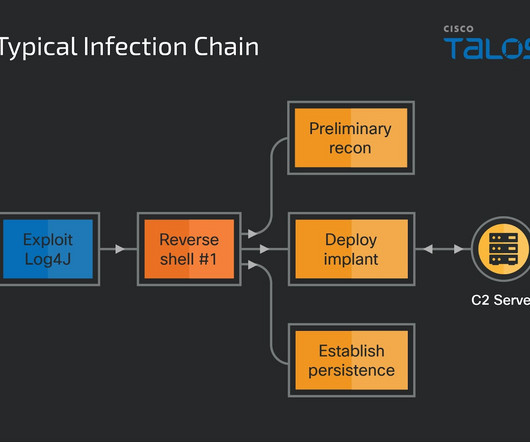
Data Privacy and Open Data: Secondary Uses under GDPR. Mitigate Data Privacy and Security Risks with Machine Learning. The Privacy and Security Dichotomy. GDPR and Cross Border Data Flows between the EU and the US: Current State of the Law. GDPR Compliance Starts with Data Discovery.











































Let's personalize your content