FBI Seizes Criminal Site BreachForums
Data Breach Today
MAY 15, 2024
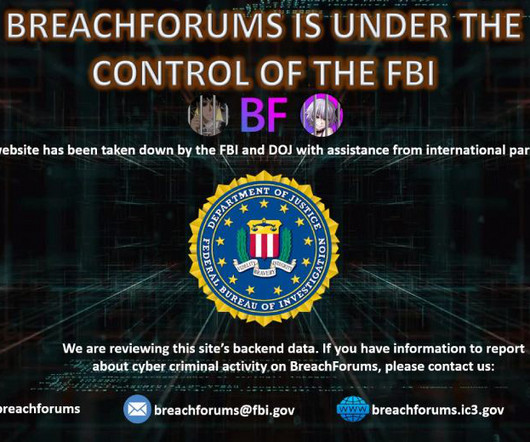
Website of BreachForums Administrator 'Baphomet' Also Appears to Be Down An international law enforcement operation shut down BreachForums, a criminal forum where hackers posted and sold the contents of hacked databases. The website of the criminal forum in its clear and dark web domains displays a seizure notice stating that it is "under the control of the FBI.






































Let's personalize your content