US CISA Aims to Expand Automated Malware Analysis Support
Data Breach Today
APRIL 10, 2024
US Cyber Defense Agency Scales Next-Generation Malware Analysis Platform The U.S.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Data Breach Today
APRIL 10, 2024
US Cyber Defense Agency Scales Next-Generation Malware Analysis Platform The U.S.

Data Breach Today
MARCH 15, 2022
The ISMG Security Report features an analysis of the U.S. government's request for billions of dollars in tech aid to curb the global impact of the Kremlin's campaign in Ukraine. It also examines Biden's cryptocurrency executive order and why breached organizations often don't share full details.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
JANUARY 19, 2023
A group of Swiss researchers have published an impressive security analysis of Threema. We provide an extensive cryptographic analysis of Threema, a Swiss-based encrypted messaging application with more than 10 million users and 7000 corporate customers.

Schneier on Security
JANUARY 2, 2024
(This is a serious analysis, and the methodology looks sound.) Future research should aim towards a more comprehensive analysis to determine the potential influence of TikTok on popular public narratives.

The Last Watchdog
JUNE 23, 2023
June 22, 2023 — Dasera , the premier automated data security and governance platform for top-tier finance, healthcare, and technology enterprises, is thrilled to unveil “Ski Lift,” a complimentary platform exclusively designed for Snowflake users. Mountain View, Calif.

Security Affairs
FEBRUARY 16, 2024
CISA revealed that threat actors breached an unnamed state government organization via an administrator account belonging to a former employee. The government experts conducted an incident response assessment of the state government organization after its documents were posted on the dark web.

Data Breach Today
NOVEMBER 8, 2019
The latest edition of the ISMG Security Report offers an analysis of how Twitter allegedly was used to spy on critics of the Saudi Arabian government. Also featured: A preview of the new NIST Privacy Framework and an update on business email compromise attacks.
Security Affairs
MARCH 28, 2024
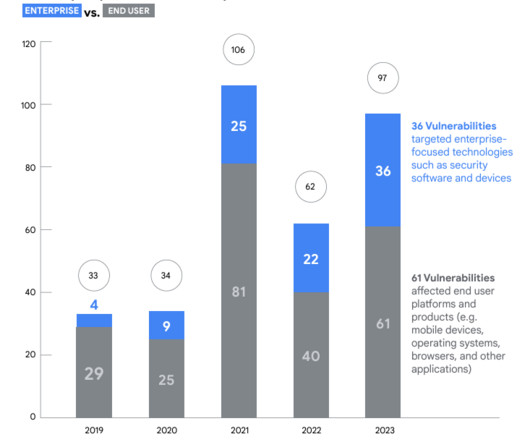
Google’s Threat Analysis Group (TAG) and Mandiant reported a surge in the number of actively exploited zero-day vulnerabilities in 2023. The Chinese government made the headlines because government-linked APT groups exploited 12 zero-day vulnerabilities in 2023, which marks a notable increase from seven in 2022.

Security Affairs
AUGUST 26, 2021
Cybersecurity and Infrastructure Security Agency (CISA) released five malware analysis reports (MARs) related to samples found on compromised Pulse Secure devices. CISA published five malware analysis reports (MARs) related to samples found on compromised Pulse Secure devices. v1: Pulse Connect Secure.
Security Affairs
AUGUST 9, 2022
Cyber Security Specialist Zoziel Pinto Freire shows an example of malicious file analysis presented during his lecture on BSides-Vitória 2022. My objective with this series of articles is to show examples of malicious file analysis that I presented during my lecture on BSides-Vitória 2022. Static Analysis x Dynamic Analysis.

Data Breach Today
JANUARY 31, 2020
The latest edition of the ISMG Security Report discusses the ramifications of the U.K's decision to allow limited use of Huawei's equipment in 5G networks. Plus: Updates on Wawa's stolen card offered for sale and nascent security threats from social networks and drones.
Security Affairs
APRIL 24, 2024
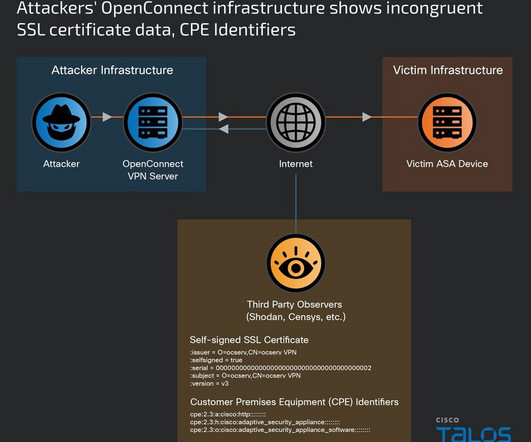
Nation-state actor UAT4356 has been exploiting two zero-days in ASA and FTD firewalls since November 2023 to breach government networks. Early in 2024, a customer contacted Cisco to report a suspicious related to its Cisco Adaptive Security Appliances (ASA). Cisco Talos researchers tracked this cyber-espionage campaign as ArcaneDoor.

Security Affairs
MARCH 19, 2024
The campaign seems active since at least early 2022 and focuses primarily on government organizations. The group often exploited access to government infrastructure to target other government entities. Analysis of the backdoors uploaded on VirusTotal revealed that threat actors utilized geopolitical topics as bait.

Schneier on Security
AUGUST 31, 2023
A used government surveillance van is for sale in Chicago: So how was this van turned into a mobile spying center? Multiple Sony DVD-based video recorders store footage captured by cameras, audio recorders by high-end equipment brand Marantz capture sounds, and time and date generators sync gathered media up for accurate analysis.
Security Affairs
NOVEMBER 16, 2023
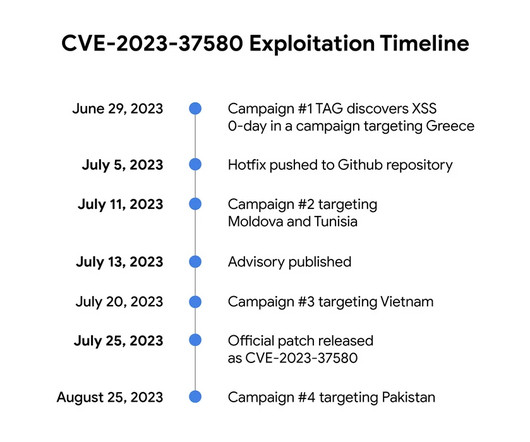
Google TAG revealed that threat actors exploited a Zimbra Collaboration Suite zero-day ( CVE-2023-37580 ) to steal emails from governments. The first campaign aimed at a government organization in Greece, threat actors sent emails containing exploit urls to their targets. ” continues the report. .”
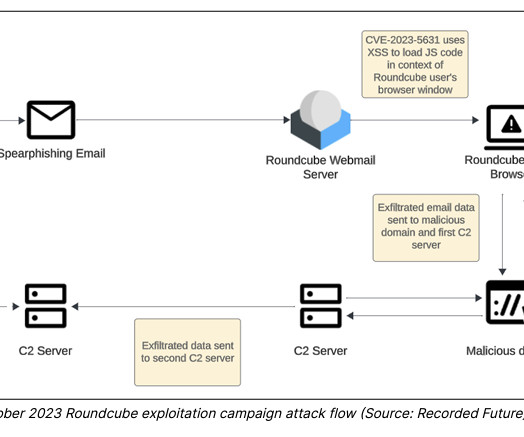
Security Affairs
FEBRUARY 19, 2024
The nation-state actors are known to carry out cyber-espionage against targeting government, military, and national infrastructure entities in Europe and Central Asia since at least December 2020. The researchers recommend reading the detailed analysis of the recent TAG-70 campaign here.

erwin
OCTOBER 31, 2019
The Regulatory Rationale for Integrating Data Management & Data Governance. Now, as Cybersecurity Awareness Month comes to a close – and ghosts and goblins roam the streets – we thought it a good time to resurrect some guidance on how data governance can make data security less scary. What data do we have and where is it?

erwin
SEPTEMBER 3, 2020
Why should you integrate data governance (DG) and enterprise architecture (EA)? Data governance provides time-sensitive, current-state architecture information with a high level of quality. Automating Data Governance and Enterprise Architecture. Data Governance and Enterprise Architecture for Regulatory Compliance.

Data Breach Today
JULY 5, 2019
The latest edition of the ISMG Security Report analyzes the debate over whether the government should require technology firms to use weak encryption for messaging applications. Plus, D-Link's proposed settlement with the FTC and a CISO's update on medical device security.

IT Governance
SEPTEMBER 7, 2023
This week, we discuss security issues at the Electoral Commission, Meta’s appeal against daily GDPR fines, and a breach affecting 10 million users of the French unemployment agency Pôle emploi. Transcript: Hello and welcome to the IT Governance podcast for Friday, 8 September 2023.

Data Breach Today
DECEMBER 20, 2019
The latest edition of the ISMG Security Report discusses the recent ransomware attacks on the city of New Orleans as well as other units of local government and schools. Also featured: discussion on security issues for IoT and legacy medical devices.

Schneier on Security
NOVEMBER 21, 2023
Google’s Threat Analysis Group announced a zero-day against the Zimbra Collaboration email server that has been used against governments around the world. TAG has observed four different groups exploiting the same bug to steal email data, user credentials, and authentication tokens. The vulnerability was discovered in June.
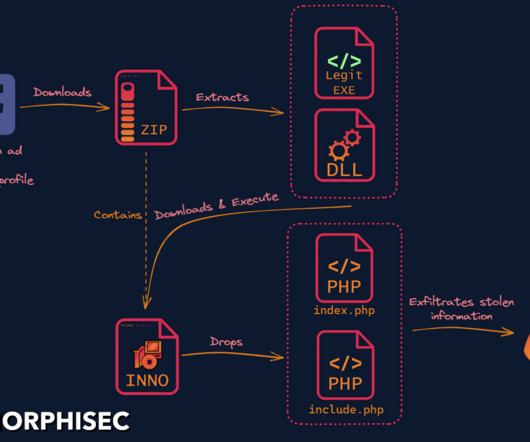
Security Affairs
MARCH 7, 2023
Researchers discovered a new info stealer dubbed SYS01 stealer targeting critical government infrastructure and manufacturing firms. ” reads the analysis published by Morphisec. to lure victims into downloading a malicious file. .”

IBM Big Data Hub
FEBRUARY 5, 2024
For federal and state governments and agencies, identity is the crux of a robust security implementation. Numerous individuals disclose confidential, personal data to commercial and public entities daily, necessitating that government institutions uphold stringent security measures to protect their assets.

Security Affairs
MARCH 9, 2022
government. government. The campaign took place in February and Google Threat Analysis Group (TAG) team was not able to link it to the ongoing invasion of Ukraine. The campaign took place in February and Google Threat Analysis Group (TAG) team was not able to link it to the ongoing invasion of Ukraine. government.
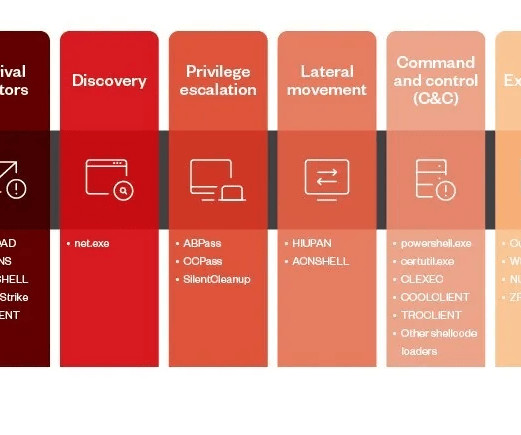
Security Affairs
MARCH 27, 2023
China-linked Earth Preta cyberespionage group has been observed adopting new techniques to bypass security solutions. Trend Micro researchers reported that the China-linked Earth Preta group (aka Mustang Panda ) is actively changing its tools, tactics, and procedures (TTPs) to bypass security solutions.

Security Affairs
MARCH 24, 2024
Every week the best security articles from Security Affairs are free for you in your email box. Government’s Antitrust Case Against Apple Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, Ramadan ) Is it a Russia’s weapon?
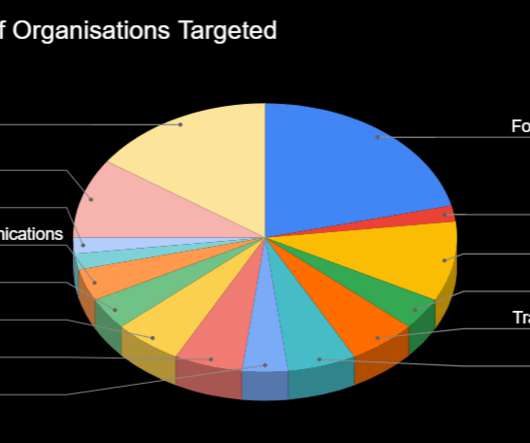
Security Affairs
SEPTEMBER 20, 2021
Security researchers uncovered a large phishing campaign targeting multiple government departments in APAC and EMEA countries. . Researchers from cybersecurity firm Cyjax uncovered a large phishing campaign targeting multiple government departments in APAC and EMEA countries. . ” concludes the analysis.

Security Affairs
JUNE 6, 2022
Following the attacks of the Killnet Collective, the group responsible for the attacks against major government resources and law enforcement, a new group has been identified called “Cyber Spetsnaz”. Sources interviewed by Security Affairs interpreted this activity with high levels of confidence to be state-supported.

erwin
APRIL 2, 2021
Data Security Starts with Data Governance. Lack of a solid data governance foundation increases the risk of data-security incidents. Without data governance, organizations lack the ability to connect the dots across data governance, security and privacy – and to act accordingly.
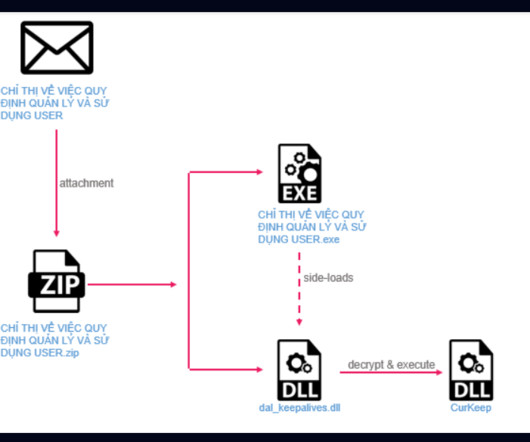
Security Affairs
OCTOBER 13, 2023
A cyberespionage campaign, tracked as Stayin’ Alive, targeted high-profile government and telecom entities in Asia. ” reads the analysis published by Checkpoint. The analysis of the C2 allowed the researchers to discover other loader variants used by the threat actor, such as CurLu, CurCore, and CurLog.

Security Affairs
AUGUST 7, 2020
Google published its second Threat Analysis Group (TAG) report which reveals the company has taken down ten coordinated operations in Q2 2020. Google has published its second Threat Analysis Group (TAG) report , a bulletin that includes coordinated influence operation campaigns tracked in Q2 of 2020. response to COVID-19.
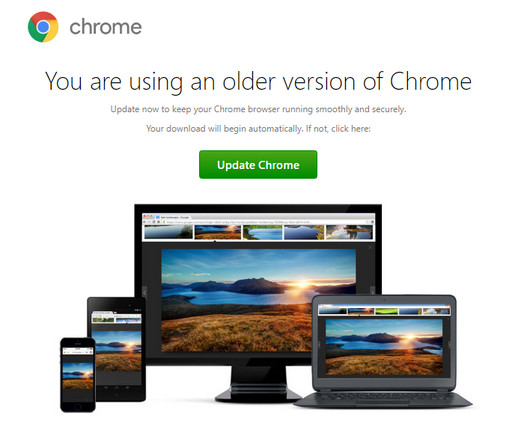
Security Affairs
NOVEMBER 21, 2023
Experts warn of a surge in NetSupport RAT attacks against education, government, and business services sectors. The most impacted sectors are education, government, and business services. ” reads the analysis published by Carbon Black Managed Detection & Response team.

Security Affairs
NOVEMBER 10, 2021
Taiwan ‘s government agencies face around five million cyberattacks and probes every day, most of them from China. Around five million cyber attacks hit Taiwan’s government agencies every day, and most of the hacking attempts are originated from China. SecurityAffairs – hacking, Taiwan Government).

Collibra
JANUARY 9, 2024
In today’s world, data drives many of the decisions made by federal and state government agencies. High-quality data about vaccine supplies and population densities can lead to a successful distribution strategy, saving lives and strengthening public trust in the government’s response to the crisis.

Data Breach Today
SEPTEMBER 24, 2021
The latest edition of the ISMG Security Report features an analysis of how the U.S. government has been tracking an increase in the pace of attacks tied to Conti ransomware. Also featured are what "protection" means today and building a new cybersecurity operating model.

erwin
OCTOBER 8, 2020
And as you make this transition, you need to understand what data you have, know where it is located, and govern it along the way. As organizations look to migrate their data from legacy on-prem systems to cloud platforms, they want to do so quickly and precisely while ensuring the quality and overall governance of that data.

Data Breach Today
OCTOBER 22, 2021
The latest edition of the ISMG Security Report features an analysis of whether businesses are stepping up their ransomware defenses in response to several warnings released by the U.S. governments highlighting the threat posed to infrastructure. Also featured are the Thingiverse data breach and airline fraud trends.

Security Affairs
FEBRUARY 28, 2024
Analyzing the Email Security Landscape and exploring Emerging Threats and Trends. VIPRE Security Group’s latest report, “Email Security in 2024: An Expert Insight into Email Threats,” delves into the cutting-edge tactics and technologies embraced by cybercriminals this year. million as malicious.

erwin
SEPTEMBER 19, 2019
Data governance isn’t a one-off project with a defined endpoint. Data governance, today, comes back to the ability to understand critical enterprise data within a business context, track its physical existence and lineage, and maximize its value while ensuring quality and security. Passing the Data Governance Ball.

Data Matters
SEPTEMBER 30, 2020
government released a “White Paper” addressing how U.S. national security law did not provide equivalent privacy protections to those available in the EU. national security law protects EU personal data. On September 28, the U.S. companies might justify their continued transfer to the U.S. To make these determinations, the U.S.
Security Affairs
SEPTEMBER 10, 2022
China-linked BRONZE PRESIDENT group is targeting government officials in Europe, the Middle East, and South America with PlugX malware. Secureworks researchers reported that China-linked APT group BRONZE PRESIDENT conducted a new campaign aimed at government officials in Europe, the Middle East, and South America with the PlugX malware.
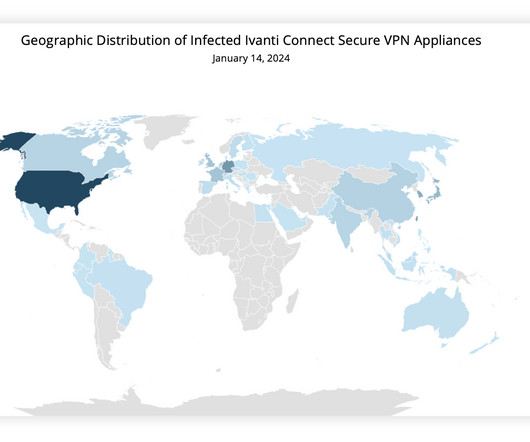
Security Affairs
JANUARY 16, 2024
Experts warn that recently disclosed Ivanti Connect Secure VPN and Policy Secure vulnerabilities are massively exploited in the wild. x and Ivanti Policy Secure. is a command injection vulnerability in web components of Ivanti Connect Secure (9.x, x) and Ivanti Policy Secure. reads the advisory published by Ivanti.

Security Affairs
MARCH 18, 2022
Google’s TAG team revealed that China-linked APT groups are targeting Ukraine’s government for intelligence purposes. Below is the tweet published by TAG chief, Shane Huntley, who cited the Google TAG Security Engineer Billy Leonard. government. ” wrote Leonard. China is working hard here too. Pierluigi Paganini.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content