Mine, Mine, All Mine
John Battelle's Searchblog
APRIL 19, 2024
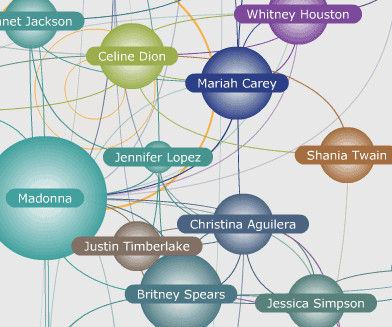
Author’s musical preferences not included… No Longer Mine When I write, I like to listen to music. I also don’t own a book collection, at least, not one I’d consider complete or accessible in the way my bookshelf was twenty years ago. The original MusicPlasma interface. But it did not happen that way.













































Let's personalize your content