Phishers Spoof USPS, 12 Other Natl’ Postal Services
Krebs on Security
OCTOBER 9, 2023
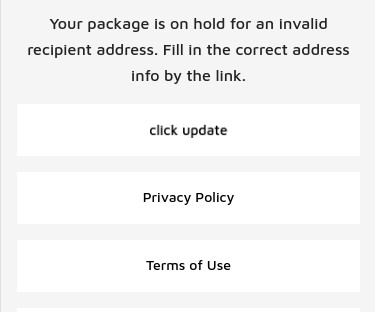
com , which DomainTools.com says was registered way back in September 2018 to an individual in Nigeria. According to dnslytics.com , that same analytics code has shown up on at least six other nearly identical USPS phishing pages dating back nearly as many years, including onlineuspsexpress[.]com














































Let's personalize your content