Cybercriminals Dive Into Cryptomining Pools to Launder Funds
Data Breach Today
JUNE 16, 2023
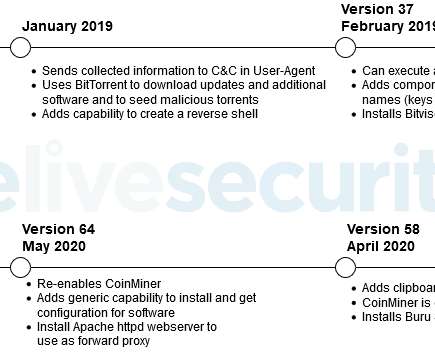
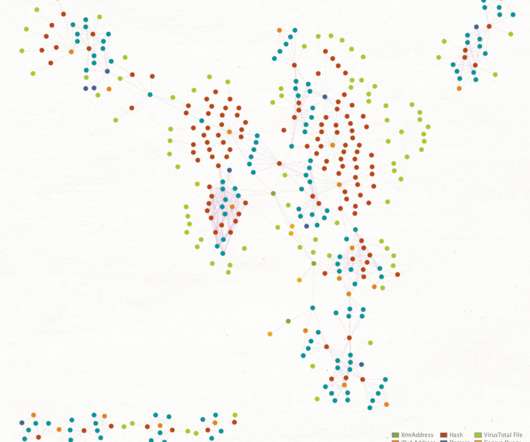
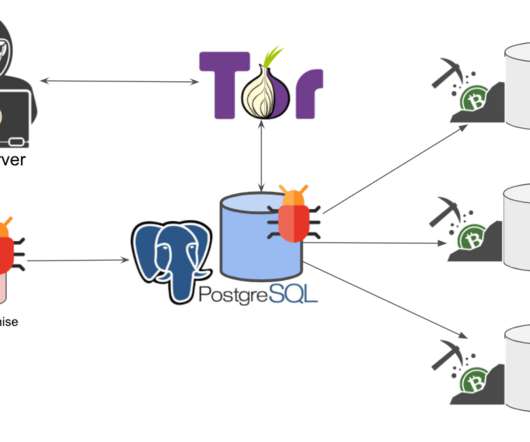
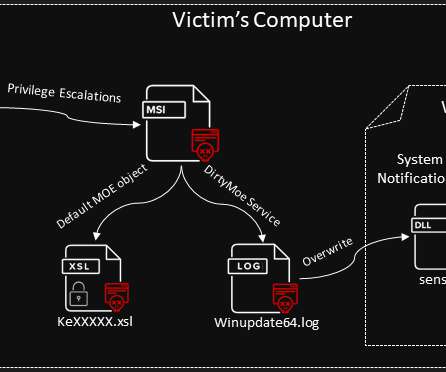
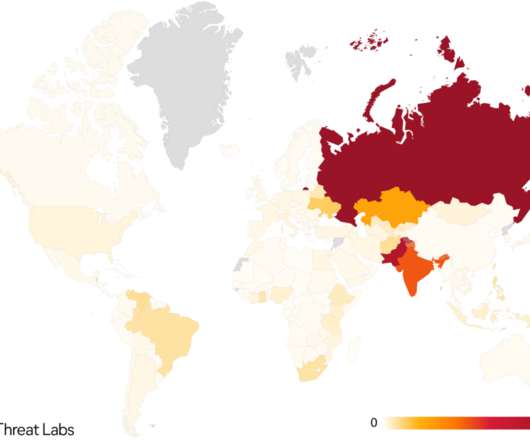
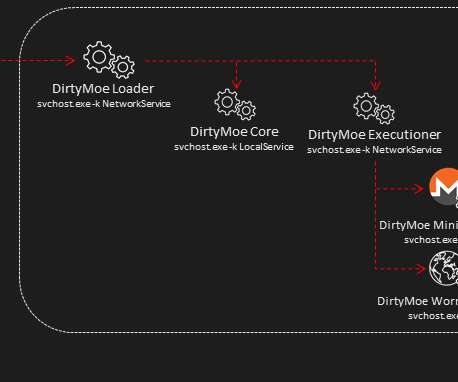
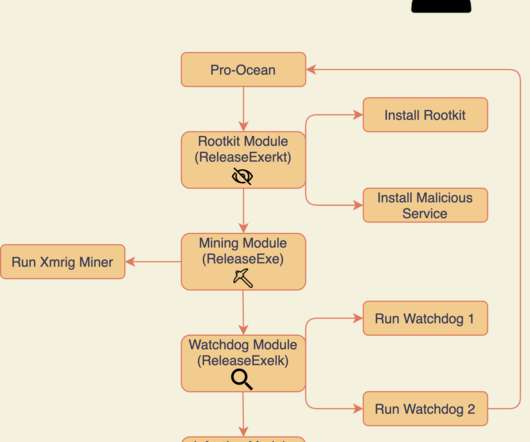
Ransomware Attackers Sent $10M to Mining Services in Q1 2023, Up From $10K in 2018 Ransomware actors are using the thing that verifies crypto transactions - mining - to their advantage.
































Let's personalize your content