Dirty Pipe Linux flaw allows gaining root privileges on major distros
Security Affairs
MARCH 7, 2022
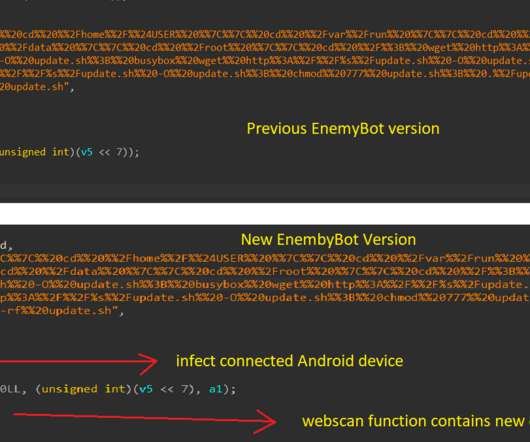
Kellerman explained that the flaw is similar to CVE-2016-5195 , aka Dirty Cow, and is more dangerous because it is easier to exploit. The CVE-2022-0847 vulnerability allows overwriting data in arbitrary read-only files, which could lead to privilege escalation because unprivileged processes can inject code into root processes.










































Let's personalize your content