SECURITY AFFAIRS MALWARE NEWSLETTER – ROUND 15
Security Affairs
OCTOBER 13, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Over 300,000!
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Security Affairs
OCTOBER 13, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Over 300,000!
Security Affairs
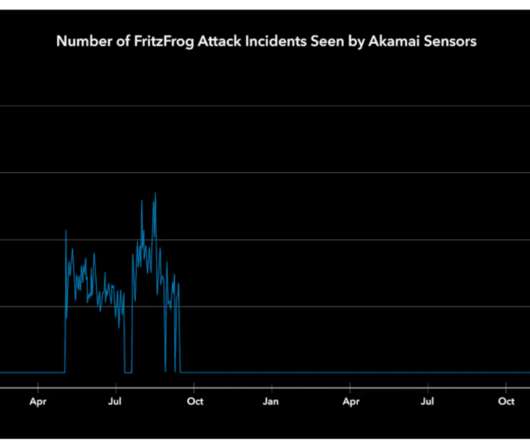
FEBRUARY 11, 2022
FritzFrog P2P botnet is back and is targeting servers belonging to entities in the healthcare, education, and government sectors. The bot is written in Golang and implements wormable capabilities, experts reported attacks against entities in the government, education, and finance sectors. ” reads the report published by Akamai.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Driving Responsible Innovation: How to Navigate AI Governance & Data Privacy
Improving the Accuracy of Generative AI Systems: A Structured Approach

IG Guru
JULY 28, 2020
NAGARA’s 2020 Summer Online Forum: Mining Our Past, Engineering Our Future is on Friday, July 31, 2020! The post NAGARA Webinar – Mining Our Past, Engineering Our Future – Registration and Fee Required – 5 Credits appeared first on IG GURU. Remember, this event has been pre-approved for 5.0

Security Affairs
APRIL 26, 2024
Emerging threats Cybercrime often exploits precisely the lack of regulation and centralized controls of cryptocurrencies to deceive investors and embezzle funds through various forms of phishing, investment scams, digital wallet theft, ransomware, and illegal mining. Education improves awareness” is his slogan.

Micro Focus
JANUARY 11, 2023
A gamut of “breaking into tech” stories exist out there; so here’s mine in hopes of both educating and inspiring others to seek professions they truly love. The post Tips for Emerging in the Technology Industry appeared first on Micro Focus Blog.

Data Matters
SEPTEMBER 11, 2018
State regulators are also investigating trading platforms or mining operations that may be operating as unregistered brokers or dealers. FINRA’s warning highlights similar themes to the mock ICO website the SEC recently launched as part of an investor education initiative. FINRA Investor Alerts. Conclusion.

IBM Big Data Hub
JANUARY 10, 2023
Grasping these opportunities at IBM, we’re increasingly building our specialism in process mining and data analysis tools and techniques we believe to be true ‘game changers’ when it comes to building cultures of continuous change and innovation. So how do you spot this early, and react or even prevent this in a timely and effective manner?

eDiscovery Daily
MARCH 25, 2020
One week from today, on Thursday, April 2 at noon CST (1:00pm EST, 10:00am PST), ACEDS will host the webinar Mining for Valuable Data – Collection Fundamentals. The post Here’s an ACEDS Houston CLE Event You Can Attend No Matter Where You Are: eDiscovery Education appeared first on CloudNine.

Security Affairs
OCTOBER 13, 2024
The Mexican Drug Cartels Want You Casio: Notice of Partial Service Outage and Information Leak Caused by Ransomware Attack He founded a “startup” to access sanctioned Russian websites: the cyber police of Khmelnytskyi region exposed the hacker Hacked ‘AI Girlfriend’ Data Shows Prompts Describing Child Sexual Abuse Malware Over 300,000!

Security Affairs
NOVEMBER 9, 2018
Italian Military Personnel and National Association of Professional Educators. Italian Military Personnel and National Association of Professional Educators. National Mining Office for Hydrocarbons & Geo-resources. National Association of Professional Educators. Exposed in the Hack: National Research Center.
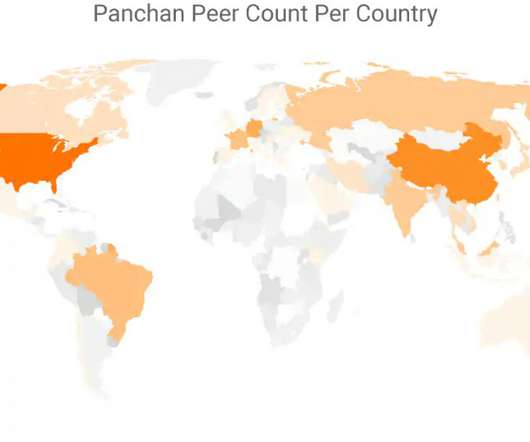
Security Affairs
JUNE 15, 2022
Researchers discovered a new Golang-based peer-to-peer (P2P) botnet, dubbed Panchan, targeting Linux servers in the education sector since March 2022. ” The botnet is engaged in cryptomining activity, the malicious code has been designed to hijack the computer’s resources to mine cryptocurrencies.

Archive-It
FEBRUARY 20, 2024
In line with our goal to make computational research (text and data mining, AI, machine learning, etc.) and education with digital collections more accessible we are introducing ARCHWay – a free to use ARCH service tier.
Security Affairs
AUGUST 28, 2023
The malware was employed in cryptocurrency mining campaigns and to launch denial-of-service (DDoS) attacks. The bot targets private gaming servers, cloud hosting providers, and certain government and educational sites. ” reads the report published by Akamai.
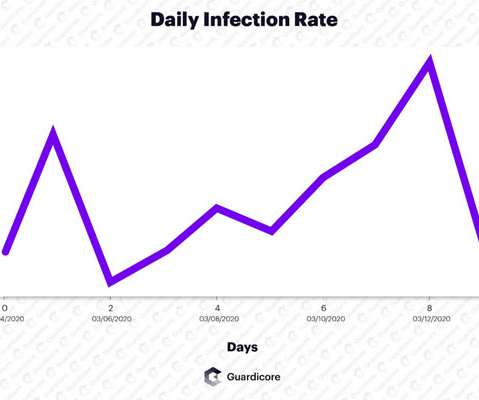
Security Affairs
APRIL 1, 2020
Cybersecurity researchers spotted a crypto-mining botnet, tracked as Vollgar, that has been hijacking MSSQL servers since at least 2018. Researchers at Guardicore Labs discovered a crypto-mining botnet , tracked as Vollgar botnet , that is targeting MSSQL databases since 2018. and Windows Script Host Object Model (wshom).

Information Management Resources
NOVEMBER 7, 2018
The ideal educational experience for today's data scientist provides the knowledge needed of statistics, database design and management, programming, data mining, visualization and predictive modeling.

Security Affairs
JULY 7, 2024
GootLoader is still active and efficient Hackers stole OpenAI secrets in a 2023 security breach Hackers leak 170k Taylor Swift’s ERAS Tour Barcodes Polyfill.io

The Last Watchdog
JULY 13, 2023
With a minimum of 50 respondents per country per industry sector, respondents represented businesses operating in: •Healthcare & Life Sciences •Manufacturing, Retail, Wholesale and Food & Beverage •Commercial Property, Real Estate and Construction •Hospitality, Entertainment and Leisure (including Gaming) •Financial Institutions and Professional (..)

Security Affairs
APRIL 28, 2023
The botnet was involved in stealing users’ credentials and data, mining cryptocurrencies abusing victims’ resources, and setting up proxies to funnel other people’s internet traffic through infected machines and routers.

eDiscovery Daily
SEPTEMBER 18, 2019
One search related to mining activities, so the attorney decided to use a wildcard of “min*” to retrieve variations like “mine”, “mines” and “mining”. Words like “mink”, “mind”, “mint” and “minion” were all being retrieved in this search for files related to “mining”. Stem Searches. Stem Searches. Other Methods.

The Schedule
JUNE 23, 2020
employee training and education. data mining. He encouraged information management professionals to consider additional uses of records beyond their typical administrative, fiscal, and legal uses, including: marketing and communications. strengthening corporate identity. documenting mission and history.

Security Affairs
OCTOBER 28, 2020
Steelcase is a US-based furniture company that produces office furniture, architectural and technology products for office environments and the education, health care and retail industries. Office furniture company Steelcase was hit by Ryuk ransomware attack that forced it to shut down its network to avoid the malware from spreading.

Security Affairs
NOVEMBER 24, 2020
” Cyber criminals also targeted crypto-mining firm NiceHash with the same technique and successfully carried out a DNS hijacking attack. . “This gave the actor the ability to change DNS records and in turn, take control of a number of internal email accounts.

Security Affairs
SEPTEMBER 19, 2018
Most of the compromised websites are e-commerce sites, but crooks also offered access to websites of organizations in healthcare, legal, education and insurance industries and belonging to government agencies. According to the experts, most of the compromised servers are from U.S., Russian, or German hosting services. .

AIIM
MARCH 19, 2020
It's also a personal belief of mine to make the most of any situation you find yourself in. And with learning on demand and how modular many educational events are, you can spread the learning over weeks or months, at a pace that works for you. That might be several hours a day freed up. Distance Learning and Social Distancing.

CILIP
NOVEMBER 13, 2020
My transition into an apprenticeship and the start of my time in the NHS followed a long journey of higher education, part-time work and an ongoing unfulfillment with my professional progress. Alongside my educational career I worked in various administration roles in different sectors which made do at the time but never left me satisfied.

Security Affairs
APRIL 30, 2023
ViperSoftX uses more sophisticated encryption and anti-analysis techniques Atomic macOS Stealer is advertised on Telegram for $1,000 per month CISA warns of a critical flaw affecting Illumina medical devices OpenAI reinstates ChatGPT service in Italy after meeting Garante Privacy’s demands Cisco discloses a bug in the Prime Collaboration Deployment (..)

Krebs on Security
NOVEMBER 21, 2020
18 Central European Time (CET), cyptocurrency mining service NiceHash disccovered that some of the settings for its domain registration records at GoDaddy were changed without authorization, briefly redirecting email and web traffic for the site. . ” In the early morning hours of Nov.

Adam Levin
SEPTEMBER 16, 2019
The data included official government ID numbers, phone numbers, family records, birthdates, death dates (where applicable), marriage dates, education histories, and work records. It contained 20.8 million records, well over the country’s current population of 16 million.

eSecurity Planet
JUNE 16, 2022
Cisco Umbrella , analyzing the threat environment for 2022, found that 86% of organizations experienced phishing, 69% experienced unsolicited crypto mining, 50% were affected by ransomware, and 48% experienced some form of information-stealing malware. Educating and training employees is a must-do in modern endpoint security.

IBM Big Data Hub
DECEMBER 15, 2023
Open-source AI projects and libraries, freely available on platforms like GitHub, fuel digital innovation in industries like healthcare, finance and education. Similarly, online educational platforms like Coursera and edX use open-source AI to personalize learning experiences, tailor content recommendations and automate grading systems.

eDiscovery Daily
SEPTEMBER 18, 2019
One search related to mining activities, so the attorney decided to use a wildcard of “min*” to retrieve variations like “mine”, “mines” and “mining”. Words like “mink”, “mind”, “mint” and “minion” were all being retrieved in this search for files related to “mining”. Stem Searches. Stem Searches. Other Methods.
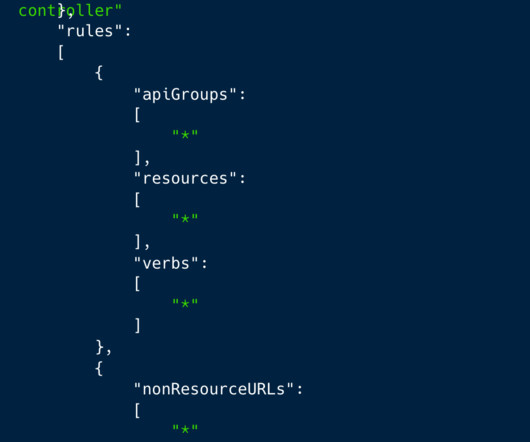
Security Affairs
APRIL 23, 2023
Experts warn of a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ). Cloud security firm Aqua discovered a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ) to create backdoors and run miners.

IT Governance
SEPTEMBER 15, 2023
Malwarebytes reports that, once installed, DarkGate Loader can be used for many nefarious purposes, including “remote access, cryptocurrency mining, keylogging, clipboard stealing, and information stealing”. You can help educate your staff with IT Governance’s Phishing Staff Awareness Training Programme.

Security Affairs
APRIL 25, 2019
Experts pointed out that attackers can exploit the vulnerabilities to take complete control over websites and servers and use them for malicious purposed, such as mining cryptocurrency or deliver malware. ” Experts found about 40,000 sites that are using the Social Warfare plugin, most of which are running a vulnerable version.

eDiscovery Daily
NOVEMBER 25, 2018
Craig Ball once made a great point in responding to a post of mine about educating lawyers when he said “ We not only need to persuade lawyers to take the plunge, we need to insure there’s a pool for them to jump into. Pursue online education? Here’s the fourth part. Do they go to a community night course on computers?

eDiscovery Daily
FEBRUARY 9, 2020
My obsession with learning all I could about a field most of us fall into rather than pursue and the event’s reputation as a party scene had encouraged me to prioritize other conferences with education sessions hyper-focused on eDiscovery throughout my first decade in the industry. — Mary Mack, CEO & Chief Legal Technologist, EDRM.

IT Governance
JANUARY 9, 2024
Source (New) Software Luxembourg Yes 3,600,000 National Automobile Dealers Association Source (New) Retail USA Yes 1,065,000 Consórcio Canopus Source (New) Professional services Brazil Yes 1,400,000 The Teaching Company (Wondrium by The Great Courses) Source (New) Education USA Yes 1.3 TB Gräbener Maschinentechnik GmbH & Co.

CILIP
APRIL 5, 2023
Similarly, the European Commission’s assessment of the evidence around its future text and data mining rules noted rightholders’ claim that an exception would “facilitate the misuse and piracy of their content and make them lose business opportunities in future”.

Info Source
MARCH 31, 2023
Over the past year, Libraries and Archiving, Education, Mining, Media Companies, and Agriculture have also demonstrated noteworthy progress towards adopting digitalisation, resulting in increased scanning needs.

erwin
JUNE 11, 2020
With tools such as Artificial Intelligence, Machine Learning, and Data Mining, businesses and organizations can collate and analyze large amounts of data reliably and more efficiently. Educators can provide a more valuable learning experience and environment for students. Transforming Industries with Data Intelligence.

ForAllSecure
AUGUST 18, 2021
Oue particular passion of mine," Easterly said, "is developing diverse organizations. In my personal opinion, this needs to be a highly ambitious national effort to be able to build a cybersecurity workforce to deal with the highly digitized world that we live in.".

Archive-It
AUGUST 16, 2023
Exploring art resources on the web as data – In July we held a workshop at the National Gallery of Art where art librarians, web archivists, students, and educators gathered to learn how to collect art resources on the web and explore them computationally at scale. Tech & Training Try it yourself: ARCH datasets and tutorials.

AIIM
JANUARY 5, 2018
The onslaught of information is burying us - we need to learn how to dig out - and mine the gold - more effectively! I contend that it is a constant education process to differentiate Information Professionals from Information TECHNOLOGY Professionals. Please provide one or two points that you will mention during your session.

eSecurity Planet
JUNE 10, 2024
The 8220 Gang, a China-based cryptojacking group, leveraged this vulnerability to take over unpatched servers for crypto-mining operations. Regularly update anti-malware software and educate your personnel about phishing dangers. With a CVSS score of 7.4, They used subtle approaches including hexadecimal encoding and HTTP via port 443.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content