Judge Orders U.S. Lawyer in Russian Botnet Case to Pay Google
Krebs on Security
DECEMBER 5, 2022
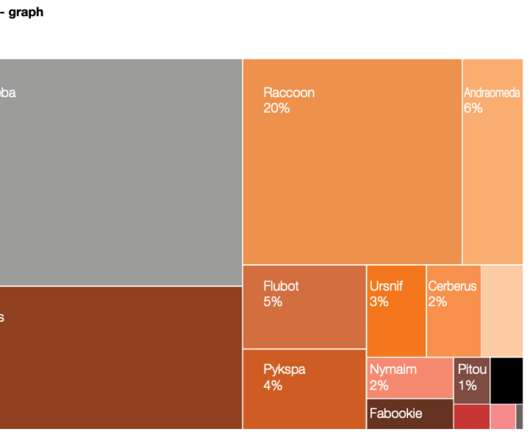
The defendants, who initially pursued a strategy of counter suing Google for interfering in their sprawling cybercrime business, later brazenly offered to dismantle the botnet in exchange for payment from Google. The judge in the case was not amused, found for the plaintiff, and ordered the defendants and their U.S.
































Let's personalize your content