New Report on IoT Security
Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”

Security Affairs
JANUARY 4, 2024
The code decodes and retrieves a shell script (“unmi.sh”) from a remote server, in turn, it fetches a configuration file for the mining activity along with the CoinMiner file hosted on GitLab. This file outlines the cryptocurrency mining setting. ” reads the analysis published by Fortinet.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
APRIL 26, 2024
Indeed, while anonymity provides privacy and security for transactions, it can also be exploited by criminals for illicit activities, such as money laundering , drug trafficking, illegal arms sales, and terrorist financing. Prevention comes through educating users and taking robust security measures to protect their digital assets.

eSecurity Planet
NOVEMBER 18, 2022
Security Forensics Investigation. He has “worked around the clock” to secure assets, identify crypto on the blockchain , find records, and work with regulators and government authorities. There were no “appropriate” security controls with digital assets. Security is another issue with the industry. Securing Crypto.

Thales Cloud Protection & Licensing
JUNE 22, 2023
How Thales and Red Hat Secure Kubernetes Data in a 5G World madhav Fri, 06/23/2023 - 05:03 The Mobile Network Operators (MNOs) that operate 5G mobile broadband networks face many challenges related to their highly distributed infrastructure. Using Kubernetes out of the box presents several challenges for security admins.

The Last Watchdog
JULY 13, 2023
Is business becoming dulled to the cyber security threat As cyber fears decrease, the technological risk landscape has fragmented, with executives nearly as concerned about the perceived threat posed by disruptive new technologies, such as AI, as the risk of cybercrime.

Troy Hunt
NOVEMBER 25, 2020
Now for the big challenge - security. The "s" in IoT is for Security Ok, so the joke is a stupid oldie, but a hard truth lies within it: there have been some shocking instances of security lapses in IoT devices. Yeah, me either, because most of mine are probably like yours: the simplest electrical devices in the house.
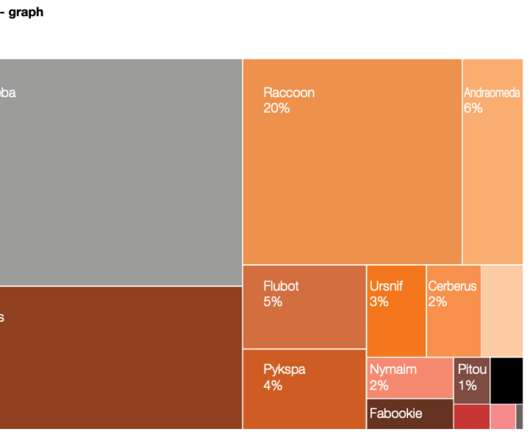
Krebs on Security
DECEMBER 5, 2022
The defendants, who initially pursued a strategy of counter suing Google for interfering in their sprawling cybercrime business, later brazenly offered to dismantle the botnet in exchange for payment from Google. The judge in the case was not amused, found for the plaintiff, and ordered the defendants and their U.S.
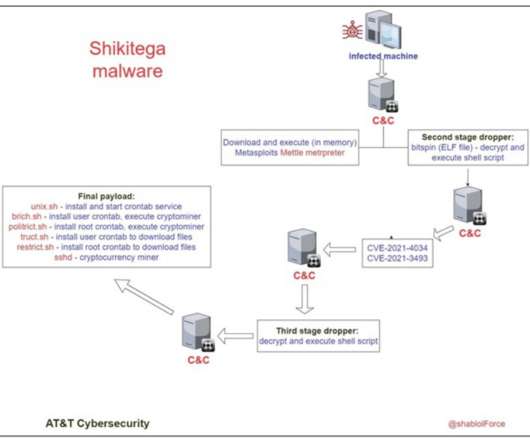
eSecurity Planet
SEPTEMBER 15, 2022
The infamous XMRig mines Monero cryptocurrency that is known to be anonymity-focused, as it’s particularly hard to trace back. This strategy seems to be a trade-off, as such services are way easier to take down by authorities, but it allows bypassing network security products that don’t block legitimate providers.

The Last Watchdog
MARCH 28, 2019
His blog, Krebs on Security , was knocked down alright. Here we are in 2019 and the same attack strategy continues to persist. It’s easy to do when there are six million open DNS resolvers on the internet using poor security practices.”. CoAP already is being discussed in security circles as the next big DDoS scaling tool.

eSecurity Planet
JUNE 16, 2022
However, basic cybersecurity tools and practices, like patching , strong passwords , and multi-factor authentication (MFA), “can prevent 80 to 90% of cyberattacks,” said Anne Neuberger, deputy national security advisor for cyber and emerging technologies, during a White House press conference in Sept. Cyberattack Statistics. Other methods.

Krebs on Security
AUGUST 12, 2020
From that story: “The reasoning behind this strategy is as simple as it is alluring: What’s not put online can’t be hacked. Postal Service, the credit bureaus or the Social Security Administration, it’s a good idea to do so for several reasons. Experian’s site also has undermined the security of the freeze PIN.
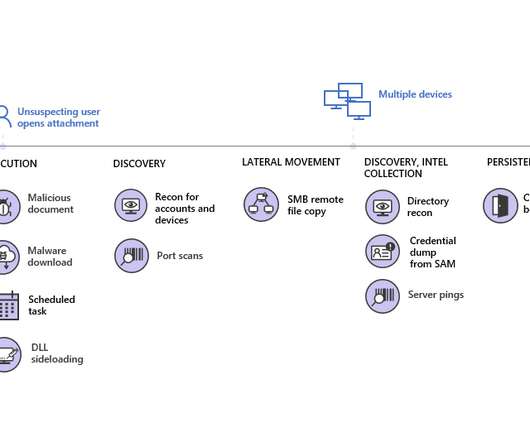
Security Affairs
DECEMBER 1, 2020
Learn how the group tried to stay under the radar using threats perceived to be less alarming: [link] — Microsoft Security Intelligence (@MsftSecIntel) November 30, 2020. The APT32 also targeted peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.

IBM Big Data Hub
NOVEMBER 24, 2023
Application modernization starts with assessment of current legacy applications, data and infrastructure and applying the right modernization strategy (rehost, re-platform, refactor or rebuild) to achieve the desired result. is a key use case that will help assist accelerated security review and approval cycles.

IBM Big Data Hub
AUGUST 14, 2023
With AI primed to take on more manual and repetitive tasks, employees surveyed report engaging in impactful work is the top factor they care about beyond compensation and job security—more important than flexible work arrangements, growth opportunities and equity. The world of work has changed compared to even six months ago.

eSecurity Planet
AUGUST 5, 2021
Two of the largest government security agencies are laying out the key cyberthreats to Kubernetes, the popular platform for orchestrating and managing containers, and ways to harden the open-source tool against attacks. ” Further reading: Top Container Security Solutions for 2021. ” Containers, Kubernetes Take Over.
eSecurity Planet
AUGUST 10, 2022
From mass production of cheap malware to ransomware as a service (RaaS) , cyber criminals have industrialized cybercrime, and a new HP Wolf Security report warns that cybercriminals are adapting advanced persistent threat (APT) tactics too. See the Best Zero Trust Security Solutions. Zero Trust Security Testing.

AIIM
DECEMBER 20, 2017
We Want Simplicity, Commitment, Strategy, and Solutions. I want a new football game and football because my little brother always tries to steal mine. So here are comments from 31 different user organizations, grouped into four gifts that they hope Santa will leave under their tree – Simplicity, Commitment, Strategy, and Solutions.

The Falcon's View
AUGUST 6, 2018
There's no shortage of guidance available today about how to structure, build, and run a security program. At end of day, the goal of your security program should be to chart a path to an optimal set of capabilities. That said, what exactly constitutes "basic security hygiene"? But, I digress. Applications. - Org Culture.

erwin
JUNE 11, 2020
Data Intelligence is the analysis of multifaceted data to be used by companies to improve products and services offered and better support investments and business strategies in place. Apply real-time data in marketing strategies. Blockchain enables more secure and complex transaction record-keeping for businesses.

Elie
MAY 30, 2018
Below are three key design strategies to help with that. Limit probing The goal of this strategy is to slow down attackers by limiting how often many payload they can test against your systems. This strategy is mostly carried out by implementing rate limiting on scarce resources such as IP and accounts. bitcoin prices.

ForAllSecure
AUGUST 18, 2021
The new Director of the Cybersecurity and Infrastructure Security Agency (CISA), Jen Easterly, opened Day 2 of Black Hat USA 2021 with a remote presentation on Hacking the Cybersecurity Puzzle. The Cybersecurity and Infrastructure Security Agency is relatively new. Easterly was appointed by Congress a few weeks ago.

Elie
MAY 30, 2018
Below are three key design strategies to help with that. Limit probing The goal of this strategy is to slow down attackers by limiting how often many payload they can test against your systems. This strategy is mostly carried out by implementing rate limiting on scarce resources such as IP and accounts. bitcoin prices.

The Texas Record
JUNE 28, 2021
ARMA defines “information governance” as “the overarching and coordinating strategy for all organizational information. After all, records management also involves security policies, regulatory compliance, and complete lifecycle management. In a nutshell, this is information governance. ” That sounds great!

Krebs on Security
JULY 18, 2023
LeakedSource also tried to pass itself off as a legal, legitimate business that was marketing to security firms and professionals. He had to demonstrate to the processor, Paypal, at the time he had a business and technical strategy to address his charge back rate.” 1 for free speech in America vs freedom of expression in Canada.”

Cyber Info Veritas
AUGUST 9, 2018
If your data and online privacy are important to you, and it should be whether you use the internet for social media, shopping, making money online, or learning, read this article with keen interest and apply the various “hacker-resistant” strategies discussed herein. Black hat hackers are the bad kind.

eSecurity Planet
JANUARY 21, 2021
Further, managing the short-term and long-term policies and procedures of your organization can be challenging without an effective GRC strategy in place. It includes multi-disciplinary risk and compliance management solutions and tools, including: IT & security risk management. IT governance and security. RSA Archer.

eSecurity Planet
JANUARY 21, 2021
Further, managing the short-term and long-term policies and procedures of your organization can be challenging without an effective GRC strategy in place. It includes multi-disciplinary risk and compliance management solutions and tools, including: IT & security risk management. IT governance and security. RSA Archer.

ARMA International
SEPTEMBER 13, 2021
The migration involves using a cloud enablement strategy to deliver products and services on-demand to business users and customers anytime, anywhere, and on any device, while evolving and adapting to business users’ and customers’ needs as new formats, standards, and devices emerge. Content Services Platforms (CSP).

Thales Cloud Protection & Licensing
JUNE 12, 2018
However, when analyzed by new algorithmic data mining methods, big data can reveal patterns, trends, and associations that can, among other things, relate to human behavior and interactions. Focus on Enhanced Security. This is how big data analytics is enabling behavioral biometric-authentication mechanisms.

The Last Watchdog
DECEMBER 14, 2023
Their guidance: Brandon Colley , Principal Security Consultant, Trimarc Security Colley Some 10-year-old vulnerabilities are still wildly prevalent. In the coming year, we also expect to see organizations work to close the disconnect between their DevOps and security teams.

CGI
JANUARY 10, 2018
Also growing at the same time is the need to store, secure, access and analyze this data. As these examples demonstrate, a strategy for ownership, access, sharing and visualization of data is needed to enable new value chains to exist. As a nearby mine expands, the entire town is being moved three kilometers from its current location.

ARMA International
DECEMBER 23, 2019
That’s no coincidence because the tenets of records management are encompassed within IG (along with legal, privacy, risk/compliance, security, technology, etc.). When you come right down to it, what we’re trying to do is: Find information when you need it, Leverage it and protect it, and Secure and assure it …. …

ForAllSecure
FEBRUARY 2, 2022
Fortunately, this is digital hardware device--the password is on a chip somewhere -- so Dan and his friend turned to a world-renowned embedded security expert, Joe Grand, who looked at the Trezor wallet. Nor am I going to wade into the debate about the ecological consequences of mining cryptocurrencies. Yeah, like that.

Everteam
JULY 11, 2019
All content management solutions from Everteam support the security and safety of the entity and its data. SAIF (Safety, Analytics and Investigation Framework) for example operates with everteam.iFile , a full-featured secured solution that supports key business processes and workflows. Future Expectations….

Thales Cloud Protection & Licensing
JULY 24, 2018
With more than 65,000 employees in 56 countries, Thales is a global leader in technology solutions for the aerospace, transport, defence and security markets. Its unique capabilities include the design and deployment of equipment, systems and services to meet complex security requirements. But, that’s not the whole story.

Information Matters
NOVEMBER 2, 2018
The market already has lots of tender portals but nobody has taken the tenders and contracts and turned them into an intelligent database which can be mined efficiently. Martin: Can you talk a bit about this strategy? We aim to help our customers to anticipate opportunities. Martin: Your primary inputs are open data feeds.

eDiscovery Daily
FEBRUARY 5, 2020
Willie J Epps , Jnr, United States Magistrate Judge, United States Western District of Missouri; Patrick Oot , Partner, Co-Chair, Data & Discovery Strategies Practice Group, Shook, Hardy & Bacon L.L.P.; Garnering strategies to help incorporate privacy engineering into product development.

Brandeis Records Manager
SEPTEMBER 10, 2015
Mine has been a positive one, and I thank the ICRM for supporting the opportunity for measurable, professional validation. Proper information retention policies are a critical aspect of your compliance strategy.”. BYOD can introduce threats to the security of your organization’s information.”. They were for me.

ARMA International
SEPTEMBER 22, 2021
Many DT journeys fail because the strategies do not properly assess the stakeholders’ needs and the organization’s capabilities. The DT journey requires a new strategy and roadmap instead of tweaking old ones. IA overlaps many areas of design, such as navigation, user experience, user interface, security model, taxonomy, and metadata.

Krebs on Security
DECEMBER 29, 2022
Until recently, I was fairly active on Twitter , regularly tweeting to more than 350,000 followers about important security news and stories here. The records also reveal how Conti dealt with its own internal breaches and attacks from private security firms and foreign governments. million users. Even though U.S.

ForAllSecure
SEPTEMBER 29, 2022
And the rest, they say is this as a reporter, I was in a position to learn as I wrote about information security. Vamosi: Welcome to the hacker mind that original podcast from for all secure. All on his own Jack discovered a security flaw in a cryptocurrency app, a flaw that opened the door to the world of bug bounties.

eSecurity Planet
JULY 25, 2023
Incident Response is a systematic method for addressing and managing security incidents in organizations, focused on minimizing and investigating the impact of events and restoring normal operations. Remote access trojans (RATs): RATs can be used to remotely gain control of a machine, placing the user’s privacy and security at risk.

CGI
JULY 5, 2018
A new and quickly spreading phenomenon is to steal computing power to mine cryptocurrencies. Cryptocurrency mining uses a lot of computing power and electricity because the mathematical problems connected to mining are difficult to solve. If you pay for the electricity and devices you use, mining will be costly.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content