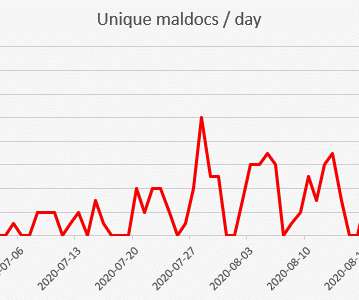
Threat actors hacked the Dropbox Sign production environment
Security Affairs
MAY 2, 2024
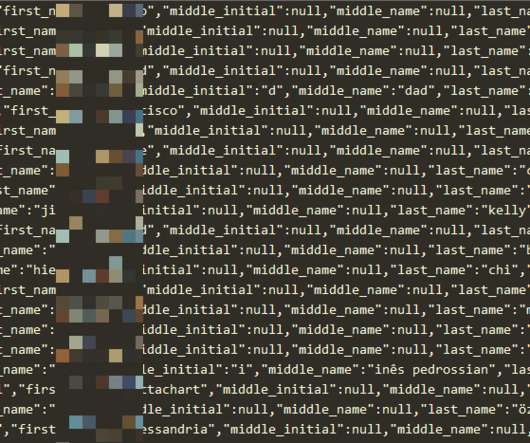
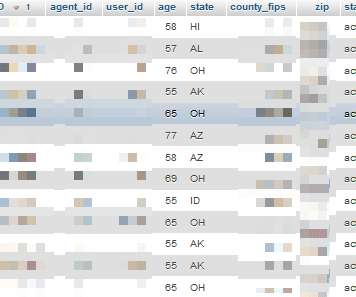
Threat actors breached the Dropbox Sign production environment and accessed customer email addresses and hashed passwords Cloud storage provider DropBox revealed that threat actors have breached the production infrastructure of the DropBox Sign eSignature service and gained access to customer information and authentication data.









































Let's personalize your content