Threat actors target K-12 distance learning education, CISA and FBI warn
Security Affairs
DECEMBER 11, 2020
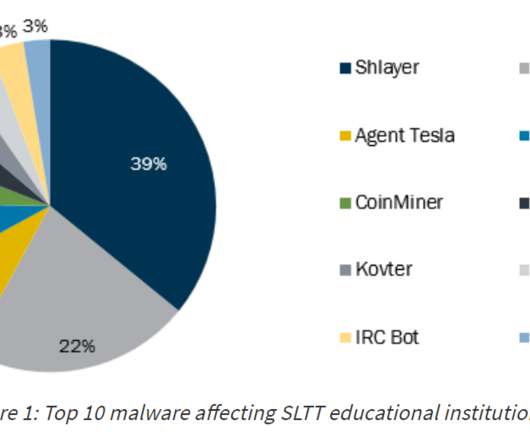
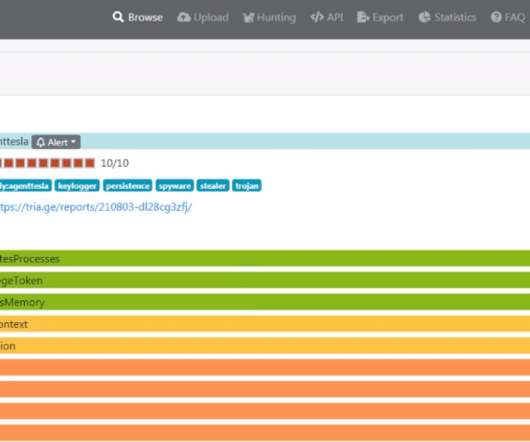
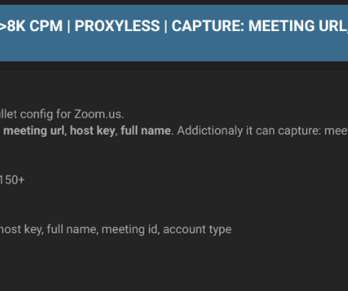
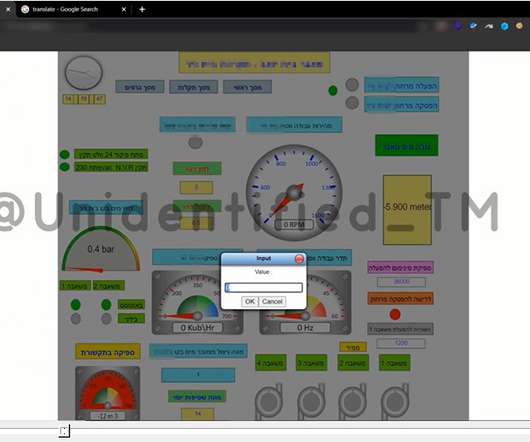
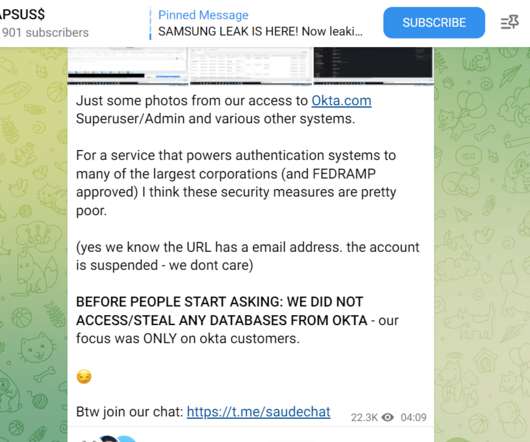
The US Cybersecurity Infrastructure and Security Agency and the FBI warned about the increase in ransomware attacks targeting the US K-12 educational sector. The US CISA and the FBI warned about the increase in ransomware attacks targeting the US K-12 educational sector aimed at data theft and disruption of distance learning services.










































Let's personalize your content