How to Prevent Malware Attacks: 8 Tips for 2023
IT Governance
APRIL 5, 2023
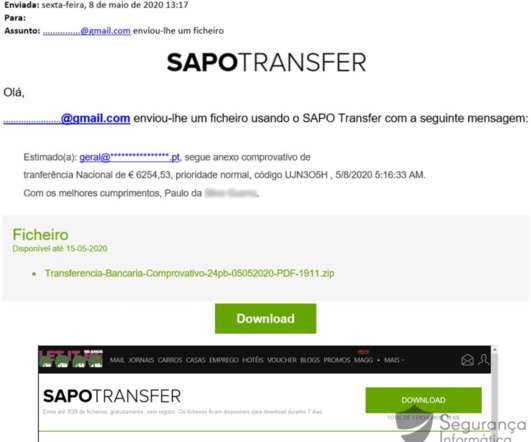
Malware is one of the most common cyber security threats that organisations and individuals face. In this blog, we explain everything you need to know about it, including our top 8 tips for preventing malware attacks. Cyber criminals include bogus links on these platforms that direct visitors to a compromised website.












































Let's personalize your content