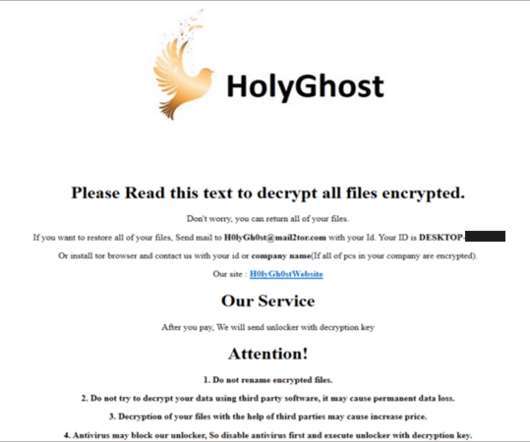
Holy Ghost ransomware operation is linked to North Korea
Security Affairs
JULY 15, 2022
The list of victims includes manufacturing organizations, banks, schools, and event and meeting planning companies. The analysis of the attackers’ wallet transactions shows that they failed to extort ransom payments from their victims. The first possibility is that the North Korean government sponsors this activity.”












































Let's personalize your content