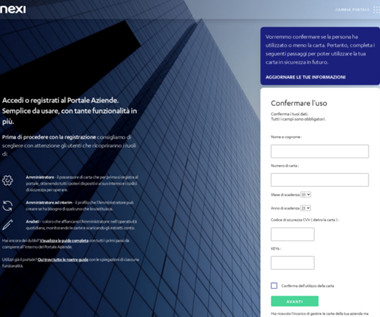
GUEST ESSAY: How to mitigate the latest, greatest phishing variant — spoofed QR codes
The Last Watchdog
NOVEMBER 6, 2023
Lieberman At this stage, companies should (at a minimum) educate their employees about the prevalence of these attacks, and the key things to look out for as the most basic form of protection against them. Staying on top of how these attacks evolve and ensuring that your defense mechanisms follow suit can feel like a full-time job.











































Let's personalize your content