Analysis: The Impact of SolarWinds Hack
Data Breach Today
DECEMBER 18, 2020
The latest edition of the ISMG Security Report features an analysis of what we know so far about the impact of the SolarWinds supply chain hack and how to respond.

Data Breach Today
DECEMBER 18, 2020
The latest edition of the ISMG Security Report features an analysis of what we know so far about the impact of the SolarWinds supply chain hack and how to respond.

Data Breach Today
JULY 9, 2021
Sizing Up the Impact of the Ransomware Attack and How to Mitigate Risks In the latest weekly update, a panel of Information Security Media Group editors discusses the repercussions of the Kaseya ransomware incident, the immediate response of the cybersecurity community and key risk management takeaways.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
FEBRUARY 24, 2023
M&T Bank's Karen Boyer on Why Check Fraud Can't Be Solved With Technology Alone Tools such as image analysis are of little help to banks dealing with check fraud since, most of the time, checks that are deposited are legitimate, says Karen Boyer, senior vice president for financial crimes at M&T Bank.

Lenny Zeltser
JANUARY 6, 2021
Malware analysis sits at the intersection of incident response, forensics, system and network administration, security monitoring, and software engineering. As someone who’s helped thousands of security professionals learn how to analyze malware at SANS Institute , I have a few tips for how you can get started.

Advertisement
How much value could you add? This framework explains how application enhancements can extend your product offerings. Just by embedding analytics, application owners can charge 24% more for their product. Brought to you by Logi Analytics.
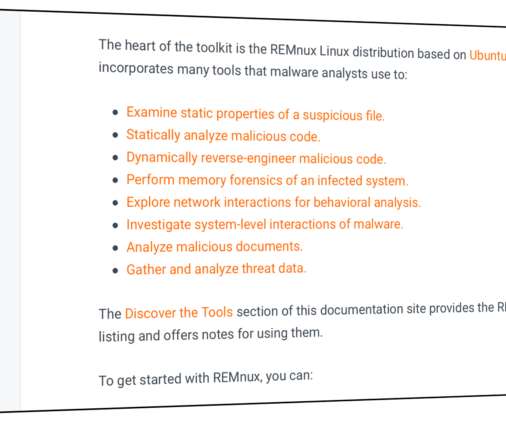
Lenny Zeltser
OCTOBER 13, 2020
How to find the right tool for the job, given how many useful utilities come as part of the distro? In addition to providing numerous tools as part of the REMnux distro, the project also offers several malware analysis tools as Docker images.

IBM Big Data Hub
JANUARY 19, 2024
Five steps to creating a strong disaster recovery strategy Disaster recovery planning starts with a deep analysis of your most critical business processes—known as business impact analysis (BIA) and risk assessment (RA). Conducting sound risk analysis (RA) is a critical step in crafting your strategy.

Advertiser: ZoomInfo
Download this ebook to learn how to maintain a strategy that includes refreshed information, database cleanses, and an accurate analysis at the same time. Forward-thinking marketing organizations have continuously invested in a database strategy for enabling marketing processes.

Advertisement
Many application teams leave embedded analytics to languish until something—an unhappy customer, plummeting revenue, a spike in customer churn—demands change. But by then, it may be too late. In this White Paper, Logi Analytics has identified 5 tell-tale signs your project is moving from “nice to have” to “needed yesterday.".

Advertiser: ZoomInfo
you’ll see what we mean in this eBook) more revenue through data-driven prospecting, stage analysis, and subsequent sales enablement. This eBook highlights best practices for developing a pipeline management process that helps sales leaders and their team C.L.O.S.E

Advertisement
Data aware: Users can combine past experiences, intuition, judgment, and qualitative inputs and data analysis to make decisions. Download the eBook to learn about How to Build Data Experiences for End Users.

Advertisement
How can you track geopolitical risk? This guide shows companies how to build out their geopolitical risk analysis – and how threat intelligence data can help supplement the analysis. And what data can you use to visualize the risk to your company? Download Now!
Let's personalize your content