How to modernize cybersecurity in higher education
Jamf
JUNE 29, 2022
Learn how to keep higher education students and educators protected, compliant, and thriving by solving key challenges and threats to cybersecurity.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

Jamf
JUNE 29, 2022
Learn how to keep higher education students and educators protected, compliant, and thriving by solving key challenges and threats to cybersecurity.

Data Breach Today
JULY 15, 2021
Rob Clyde of ISACA discusses his ideas for how to raise up the next generation of "cyberwarriors" to serve on the front lines of active defense against cyberthreats.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Breach Today
MAY 1, 2023
Tom Scanlon of Carnegie Mellon University on New Certificate Program There is a growing need for "citizen data scientists," such as engineers and programmers, to better understand the inner workings of AI and ML as those technologies become more ubiquitous, said Tom Scanlon, technical manager of the CERT data science team at Carnegie Mellon University. (..)

Jamf
APRIL 9, 2024
The 2024 Jamf Event showed how to transform learning for students, teachers and parents; better protect students; and maintain seamless, secure access.

Data Breach Today
NOVEMBER 20, 2018
Wombat's Gretel Egan on How to Take a Fresh Approach to the Awareness Challenge As attackers increasingly take advantage of users' risky behavior, enterprise security leaders are taking steps to improve end-user security education. Gretel Egan of Wombat Security outlines how to focus on education strategies that are truly effective.

AIIM
JUNE 22, 2018
With the problem growing, and the attacks getting more sophisticated, there has never been a better time to learn how to defend your business’s data and protect your employees. In this article, we will examine how to educate your employees so that a lethal hack does not disrupt your business. It’s All About Passwords.

AIIM
SEPTEMBER 7, 2021
How to Avoid Information Governance Pitfalls. We'll explore why these challenges occur, how to avoid or overcome them, and actions you can take now to get started. How to Avoid/Overcome: Overcome this issue by addressing objections directly with good communication and contextual education. Lack of Stakeholder Support.

Jamf
SEPTEMBER 28, 2022
Suraj Mohandas, Aaron Webb, Dr. Emily McRoberts-Froese, Mike Lawrence and Valeria Tschida team up to update us on new Jamf School and Jamf Pro features, how to get involved with the Jamf education community and our community education initiatives.

Jamf
SEPTEMBER 27, 2023
Dive into modern methods of device security in Education using Jamf. Learn how to create a secure digital environment for teachers and students.

Security Affairs
MARCH 12, 2024
How to defend yourself against these scams The Postal Police recommends to beware of overly tempting offers and to always check the seriousness and reliability of the interlocutor. Education improves awareness” is his slogan. He is also the author of the book “La Gestione della Cyber Security nella Pubblica Amministrazione”.

Lenny Zeltser
MAY 11, 2023
Too many people are unsure how to enter or grow in the cybersecurity industry. It’s also hard to determine how to turn a series of successive jobs into a career. Those seeking guidance can turn to professional security organizations that offer educational and networking opportunities.

KnowBe4
NOVEMBER 16, 2023
Yet, there are also those users who, despite repeated education efforts, habitually fall prey to phishing emails and simulations, neglecting the tell-tale signs of social engineering. Within our organizations, there are those employees who consistently exhibit mindfulness, avoiding every phishing attempt.

IT Governance
APRIL 5, 2023
IT Governance Podcast 2023-7: Capita, ChatGPT and TikTok (yet again) 5th April 2023 How to Prevent Malware Attacks: 8 Tips for 2023 5th April 2023 List of Data Breaches and Cyber Attacks in March 2023 – 41.9 Provide staff awareness training : Educating employees about cyber security best practices is important to help prevent cyber attacks.

Jamf
MARCH 19, 2020
To best keep students and educators safe — schools are re-evaluating their teaching practices and learning environments to accommodate an at-home, virtual learning experience. In part one of our five-part blog series, we show you how to set remote learning expectations for students and teachers.

Record Nations
JULY 8, 2019
The Family Educational Rights and Privacy Act (FERPA) (20 U.S.C. Part 99) is a federal law that protects the privacy of student records by prohibiting schools from disclosing the personally identifiable information in student education records. 1232g; 34 C.F.R.

Security Affairs
APRIL 13, 2023
Knowing how to fight them off is entirely another. The question isn’t why to build out an insider threat prevention program: it’s how. The origin and impact of insider risk To understand best how to combat them, it helps to know where insider threats originate and why. Knowing that insider threats are a risk is one thing.

Preservica
NOVEMBER 30, 2021
We have compiled a series of videos, from users in City and County Government to share how they quickly and easily perform common electronic records preservation and access tasks with Preservica’ s solutions. How to fill a research request: Probate Estate Case Files. Watch her video below to learn how to do this yourself.

The Last Watchdog
NOVEMBER 6, 2023
Lieberman At this stage, companies should (at a minimum) educate their employees about the prevalence of these attacks, and the key things to look out for as the most basic form of protection against them.

Jamf
MARCH 20, 2020
To best keep students and educators safe — schools are re-evaluating their teaching practices and learning environments to accommodate an at-home, remote learning experience. In part two of our five-part blog series, we show you how to facilitate engaging discussions daily for students and teachers.

Jamf
OCTOBER 9, 2018
To help district leaders, IT, instructional technologists and teachers get the most out of their education technology initiatives, we put together several resources explaining best practices for deploying, securing and managing iPad.

Jamf
DECEMBER 2, 2021
Learn why cybersecurity in schools is crucial for student success, and how to strengthen your defenses against the threat of lost learning time and data breaches.

Dark Reading
APRIL 27, 2021
Let's teach students how to teach themselves. Once we do that, we will have taught a generation of students how to think like hackers.

IT Governance
SEPTEMBER 24, 2019
The latest guidance from the government will assess the way further education providers are preparing for the UK’s departure from the EU, and it’s currently running a survey to get input from those looking for advice. The government’s advice will be invaluable for understanding how to manage your data protection requirements.

OpenText Information Management
JUNE 23, 2021
In recent years, those of us in software education have been debating how to make training more effective, moving towards gamification, modularizing/chunking content, creation … The post How to effectively deliver virtual training appeared first on OpenText Blogs.

Dark Reading
FEBRUARY 27, 2023
Build a playbook for employees on how to handle suspicious communications, use mail filters, and screen and verify unfamiliar calls to bolster a defensive social engineering security strategy.

Jamf
APRIL 29, 2022
Learn how to deploy Jamf Protect with Jamf School to fortify the security posture of your devices while managing your fleet, allowing students and educators to learn and teach without compromises to productivity or endpoint security.

Security Affairs
APRIL 30, 2023
Credit: ESA – European Space Agency The offensive cybersecurity team at Thales demonstrated how to take control of the ESA satellite, the is considered the world’s first ethical satellite hacking exercise. Artist’s impression of OPS-SAT. The exercise aims at assessing the resilience of satellites to cyber attacks. .”

Preservica
NOVEMBER 29, 2021
We have compiled a series of videos, from users in City and County Government to share how they quickly and easily perform common electronic records preservation and access tasks with Preservica’ s solutions. How to preserve social media content: Twitter records. Watch the video below to learn how to do this yourself.

Data Breach Today
AUGUST 13, 2021
Rebecca Herold, host of the podcast show "Data Security and Privacy with the Privacy Professor," weighs in on the state of cybersecurity and privacy education and gives her recommendations on how to remedy the many issues the security community faces today.

eDiscovery Daily
APRIL 4, 2024
Focused on innovation and education, he co-founded ESI Analyst, now CloudNine Analyst, as well as Wave Software and the Master’s Conference. The post How to Evaluate Technologies and Companies for Public Records/FOIA Requests appeared first on CloudNine.

IBM Big Data Hub
JUNE 26, 2023
Possibilities are growing that include assisting in writing articles, essays or emails; accessing summarized research; generating and brainstorming ideas; dynamic search with personalized recommendations for retail and travel; and explaining complicated topics for education and training.

IT Governance
SEPTEMBER 8, 2021
Educate employees on their responsibilities. So how should organisations approach employee education? You can learn more about the compliance risks of hybrid working by watching How to Navigate and Implement a Successful Hybrid Workforce. Beware of elevated privileges. Looking for more advice?

IT Governance
AUGUST 2, 2018
To support the wider education sector with data protection and cyber security, we are launching a sector specific email newsletter and blog series. How to sign up. To sign-up, send us ideas of what you would like us to cover or questions for us to answer, please leave complete this form and choose education as your sector.

Jamf
MARCH 25, 2020
To best keep students and educators safe — schools are re-evaluating their teaching practices and learning environments to accommodate an at-home, remote learning experience. In the conclusion of our five-part blog series, we show you how to leverage apps and games to enhance remote learning.

Rippleshot
SEPTEMBER 20, 2019
That's why we're also here: To help you educate your customers and members when the next big data breach happens — and what to do about it. We also recognize the reality that data breaches happen when gaps exist in other organization's security protocols, which can leave your own customer's sensitive data vulnerable.

Preservica
NOVEMBER 9, 2021
This educational series will regularly feature new video assets. Check back to see what’s new! As always, you can try Preservica Starter with up to 5GB archival storage, FREE forever. Get Started on your project today.

eSecurity Planet
OCTOBER 26, 2023
Also read: 19 Different Types of Malware Attacks: Examples & Defenses Best Antivirus Software Solutions How to Remove Malware on Windows (PC) Removing malware from a Windows PC requires a systematic approach to ensure the malicious software is eradicated. Educate Yourself Knowledge is a powerful defense against malware.

eSecurity Planet
SEPTEMBER 8, 2023
Technology reviews can be a temptingly easy way to gain insight into the often impenetrable world of enterprise cybersecurity products, but you need to know how to use them. To help, we’ll cover the pros, built-in biases, and suitability of each type of technology review and how to use each review type as a buyer.

eSecurity Planet
JUNE 23, 2023
Also read: 9 Best Penetration Testing Tools 24 Top Open Source Penetration Testing Tools How to Implement a Penetration Testing Program in 10 Steps Third-Party Vendor Tests: Challenges and Maximizing Value Many organizations prefer to perform in-house penetration tests because of the challenges with third-party vendors.
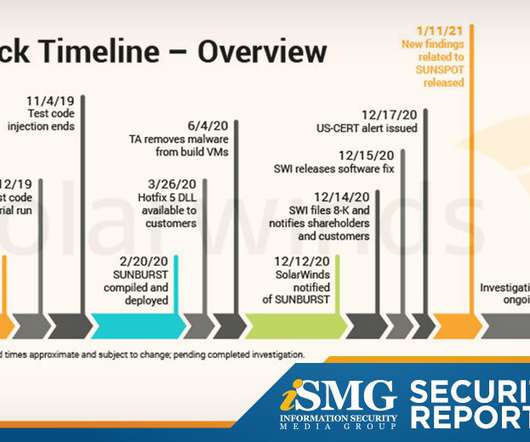
Data Breach Today
JANUARY 15, 2021
Also featured: A discussion of why security education is so crucial in 2021 and tips on how to retain SOC analysts. The latest edition of the ISMG Security Report describes new details emerging from the SolarWinds supply chain hack investigation.

IT Governance
SEPTEMBER 1, 2021
According to a recent Field Effect Software survey , 27% of respondents said they are looking to outsource some or all of their cyber security operations, compared to 24% that are investing in ongoing cyber security education and 23% that are increasing their IT or security budget. Get started.

Data Breach Today
OCTOBER 11, 2022
Fraud education expert Andi McNeal shares insights on what anti-fraud practitioners are expecting over the next year, the types of fraud to watch out for and how to mitigate fraud risks.
Docuware
SEPTEMBER 27, 2023
When computer software can use data to make an educated decision, the result is increased business productivity. The machine completes certain tasks faster than its human counterparts ever could, and people can direct their attention to all of the important work that machines can’t do.

The Last Watchdog
JANUARY 13, 2021
The question isn’t whether we should educate children about online safety, but how we can best inspire them to learn to be thoughtful, careful, and safe in the cyber world for their lifetime. As adults, we know that bad online decisions can have negative or dangerous effects for years to come.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content