500M Avira Antivirus Users Introduced to Cryptomining
Krebs on Security
JANUARY 8, 2022
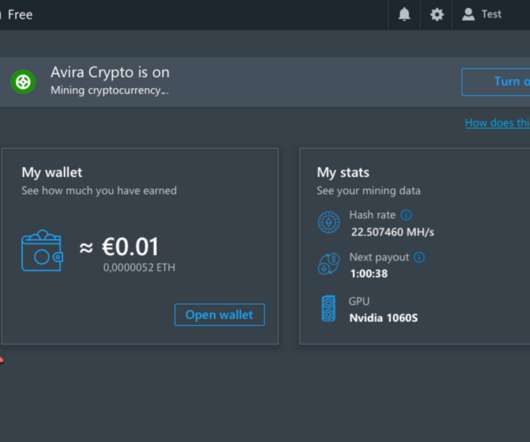
Many readers were surprised to learn recently that the popular Norton 360 antivirus suite now ships with a program which lets customers make money mining virtual currency. which was renamed to NortonLifeLock in 2019. Even with compatible hardware, mining cryptocurrencies on your own can be less rewarding.














































Let's personalize your content