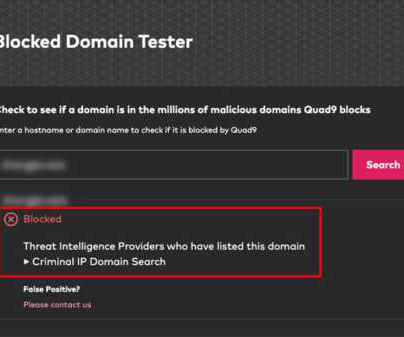
News alert: Criminal IP and Quad9 collaborate to exchange domain and IP threat intelligence
The Last Watchdog
MAY 13, 2024
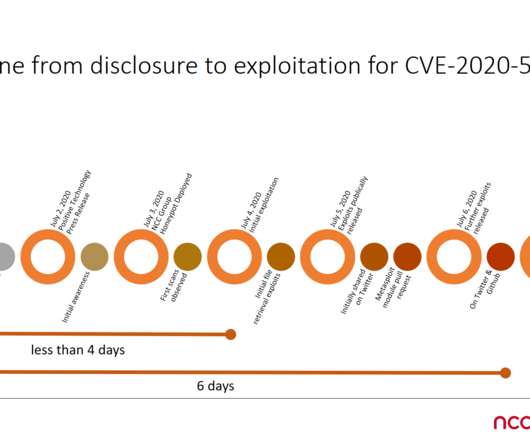
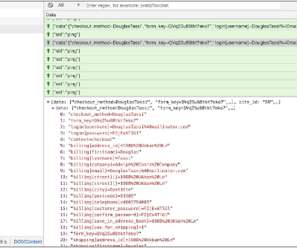
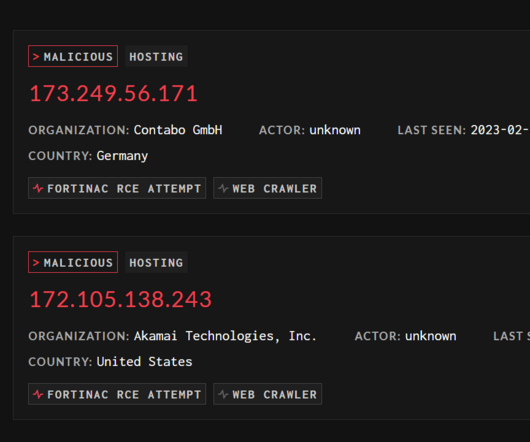
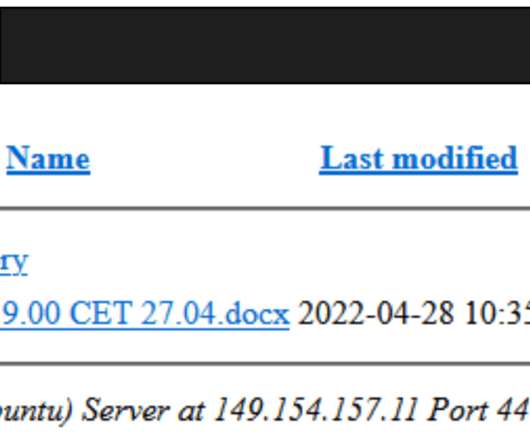
May 13, 2024, CyberNewsWire — Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA, has recently signed a technology partnership to exchange threat intelligence data based on domains and potentially on the IP address to protect users by blocking threats to end users. Torrance, Calif.,










































Let's personalize your content