IBM Cost of a Data Breach study: average Cost of Data Breach exceeds $4.2M
Security Affairs
JULY 28, 2021
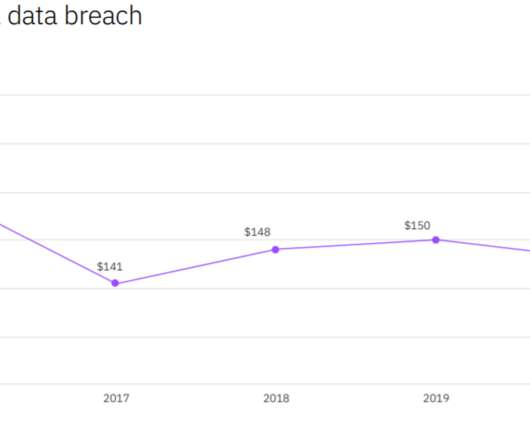
The ‘Cost of a Data Breach’ report commissioned by IBM Security states that the cost of a data breach exceeded $4.2 The study highlights the significant impact of the ongoing pandemic on the cost of data breaches and the effort to contain them. ” states IBM Security. ” states IBM Security.















































Let's personalize your content