How the new Spirion-Thales partnership enables sensitive-data-centric encryption
Thales Cloud Protection & Licensing
JUNE 29, 2022
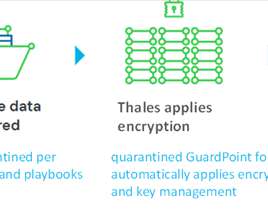
How the new Spirion-Thales partnership enables sensitive-data-centric encryption. Encryption achieves this goal by making the data readable only to those individuals with the proper access levels. It’s a similar overreach to encrypt all the data your company collects, but many organizations are doing just that.














































Let's personalize your content